1.5m spam emails sent from compromised University accounts
With the increasingly common spamming as a service underground propositions relying on botnets, and services offering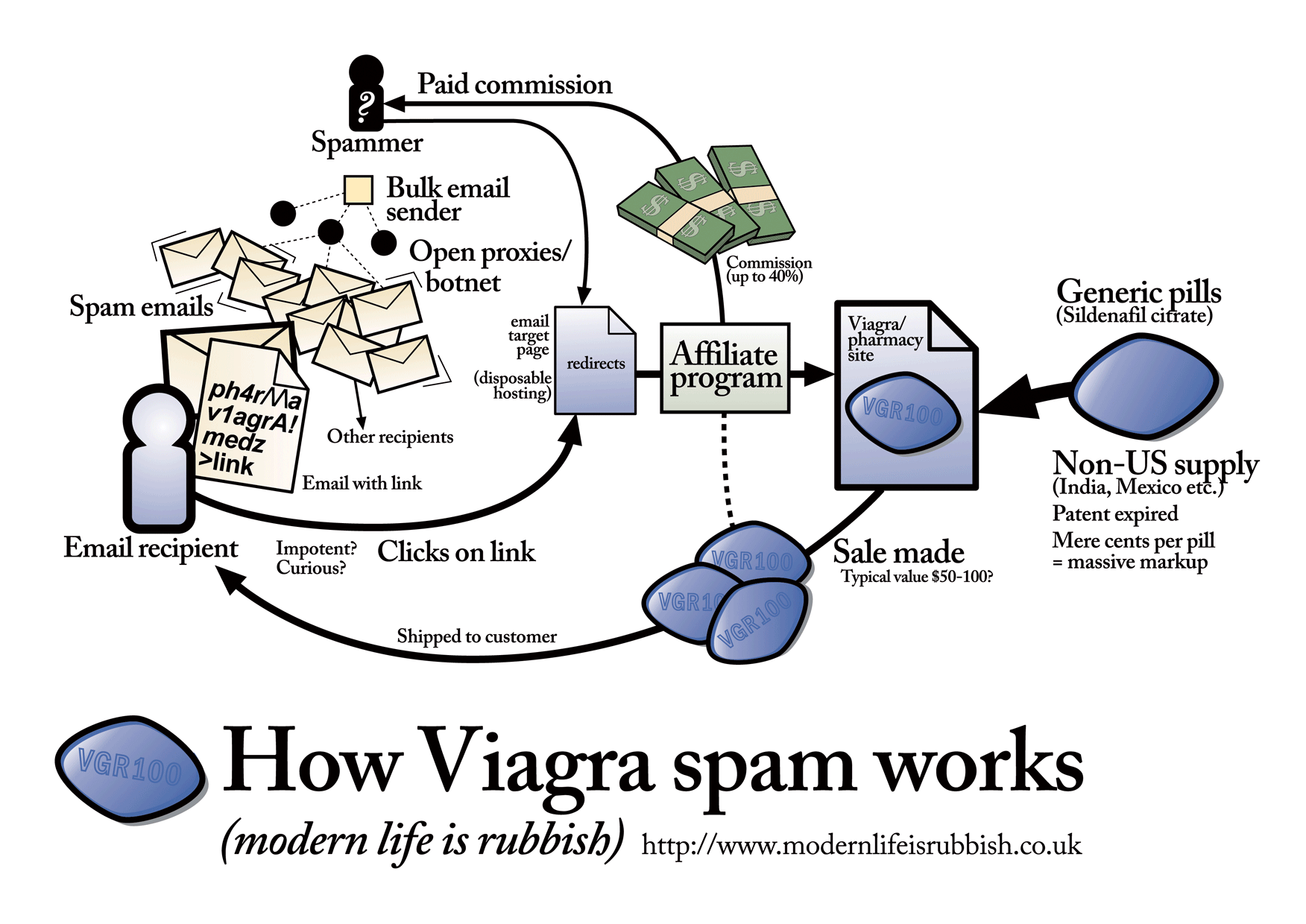
By personalizing phishing emails (spear phishing) impersonating the University of Otago, spammers managed to obtain the passwords of four staff members, whose accounts were used to send 1.5m spam emails in 60 hours during the last couple of days.
"Hackers gained access to the University of Otago staff email server recently and used it to send out an estimated 1.55 million spam emails in 60 hours, after tricking four staff members into revealing their login details. The huge volume of spam mail resulted in legitimate emails being rejected or delayed by other systems, information services manager Mike Harte said. They were re-sent once the spam attack was over. The staff members responded to "spear phish" emails which claimed to be from the IT department and asked people to reconfirm their user names and passwords or their email access would be withdrawn."
The spammers didn't just abuse the clean IP reputation of the University, they also had its mail servers blacklisted thereby causing a DoS attack to its staff and students. The University's official notice of the incident :
"The university is currently experiencing access and delivery issues with Stonebow webmail. A number of Stonebow accounts have been compromised by staff members responding to a phishing email. These accounts have been used to distribute spam. This has resulted in the university mail server being blacklisted by a number of providers. ITS has disabled those accounts affected and temporarily disabled off campus access to Stonebow webmail as the spammers are actively moving from one account to another. ITS is working to get the university removed from the blacklists.
ITS will monitor service providers that do not accept email from Otago and work with them to re-establish email services in the coming few days. If any administrators are in contact with staff currently overseas, please advise them of the current email situation."
Theoretically, the tools and the motivation to abuse the access to compromised accounts have always been there, but such attempts are more of a fad rather than a trend, since these days spammers are actively outsourcing the entire process of botnet creation and supply of new bots with clean IP reputations to malware authors. How come? It's far more cost-effective than having to do it on their own.