200,000 sites spreading web malware, China's hosting the most
Yesterday, the Stopbadware.org initiative released a report entitled "May 2008 Badware Websites Report" summarizing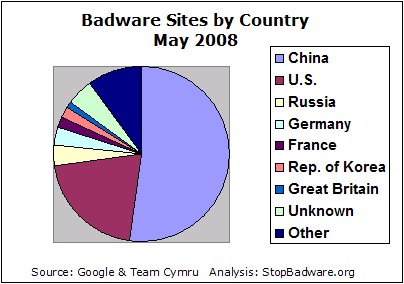
Using data from Google’s Safe Browsing initiative, StopBadware.org analyzed over 200,000 websites found to engage in badware behavior. The analysis found that over half of the sites were based on Chinese network blocks, with a small number of blocks accounting for most of the infected sites in that country. The U.S. accounted for 21% of infected sites, and these were spread across a wide range of networks. Compared to last year, the total number of sites was much higher, likely due both to increased scanning efforts by Google and to increased use of websites as a vector of malware infection. Several U.S.-based network blocks that were heavily infected last year, including that of web hosting company iPowerWeb, whose network block topped last year’s list, no longer host large numbers of infected sites.
What's important to take into consideration when going through these stats, is that a great deal of networks hosting domain portfolios engaging in a countless number of malicious activities, would remain underreported due to the efforts them put into evading common detection approaches, the result of which is their current placement in the "Unknown" and "Other" categories. I was pleasantly surprised to see SoftLayer mentioned, in fact SoftLayer's response to the research at the first place, as if we are to play a game of associations the first things that come to my mind when I see SoftLayer are The Russian Business Network, InterCage, Inc., Layered Technologies, Inc., Ukrtelegroup Ltd, Turkey Abdallah Internet Hizmetleri, and Hostfresh, ISPs providing infrastructure to malware command and control interfaces and malicious domains used in the majority of malware embedded attacks during the entire 2007, and early 2008.
The report makes an important point, namely, that compared to the previous year the total number of sites found to engage in badware activities was much bigger, mostly because of the increasing use of sites as infection vectors, but also because of Google's increased scanning efforts.
Don't forget that these are only the detected sites spreading malware, and with the ongoing efforts by malicious parties to implement evasive tactics in order to fool client side honeypots crawling their malicious sites, the number of malware spreading sites is much higher. For instance, for the past couple of weeks I've been analyzing malicious doorways which when properly analyzed redirect to over 10 to 20 different malware serving domains, and given most of them are also used as redirectors, analyzing a single malicious doorway ends up with a portfolio of over a 100 malicious domains. So what? Basically, the ongoing collaboration between blackhat search engine optimizers and malware authors, results in the malware authors getting empowered with know-how on cloaking their malicious doorways from search engine crawlers, and it's these search engine crawlers who make it possible for client side honeypots to verify whether or not a site is malicious or not. The doorway would serve legitimate content to a potentially identified search engine's crawler or even a client side honeypot, but would reveal it's real ugliness to the average Internet user.
Anyway, what's more disturbing at the bottom line - the fact that legitimate sites are starting to host most of the web malware these days, ruining the stereotype of "don't visit unknown sites or you risk getting infected with something", or the fact that we are not emphasizing on the average time it takes to shut down such a site at the first place, but are always curious where are they hosted geographically?
Consider going through the report, it's well worth it.