25 GPUs devour password hashes at up to 348 billion per second

A combination of hardware and cloud technologies could force the IT industry to rethink what constitutes a secure password.
A presentation at the Passwords^12 Conference in Norway, security researcher Jeremi Gosney demonstrated the password-cracking software HashCat on a system made up of five 4U servers kitted out with 25 AMD Radeon-powered GPUs linked together using an Infiniband switched fabric link.
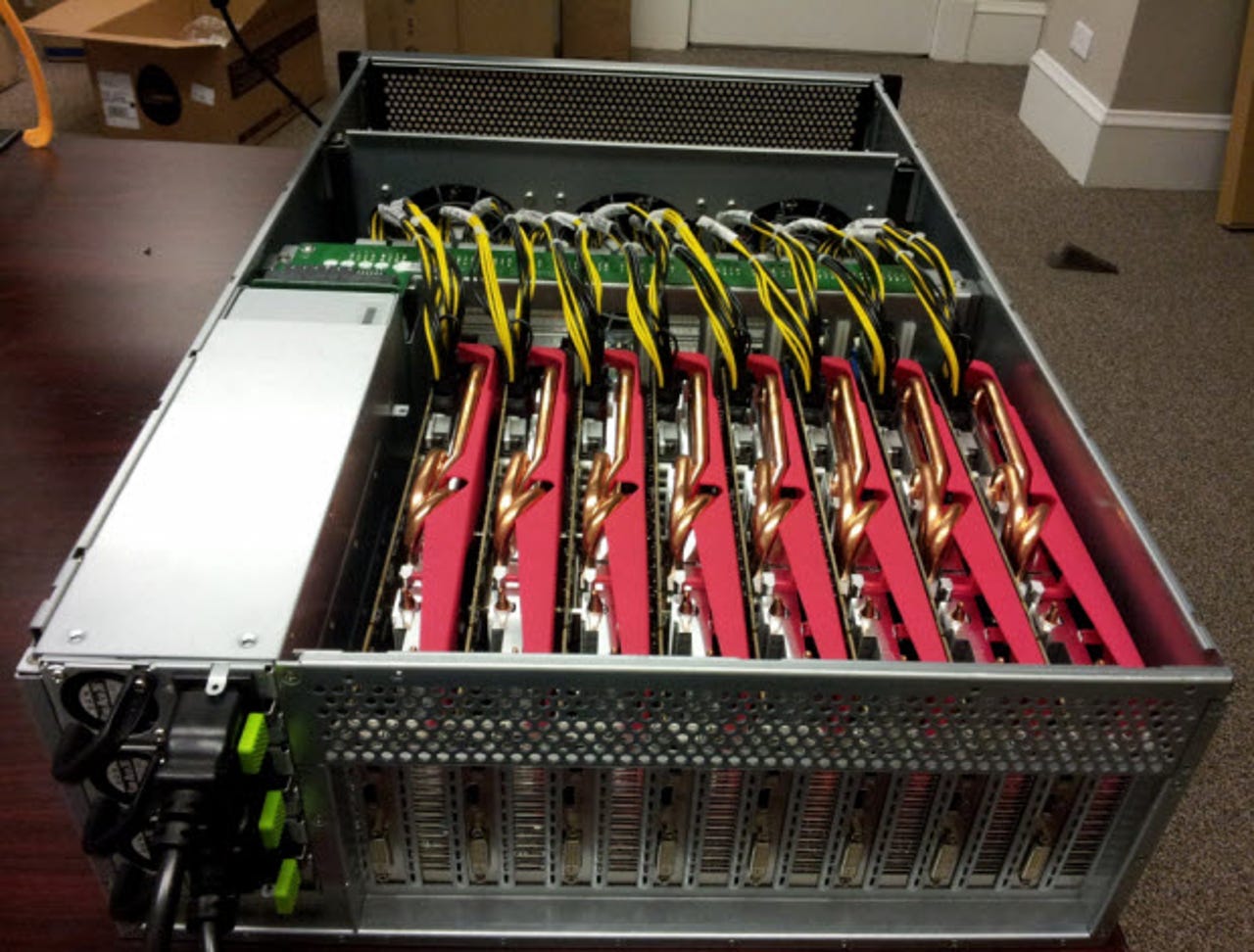
Virtual Open Cluster (VCL) software is used to load balance across the cluster.
This system doesn't just crack passwords; it literally obliterates them. The system can crunch through 348 billion NT LAN Manager (NTLM) password hashes every second. In the real world, this translates into being able to break a 14 character Windows XP password in six minutes.
The system can also tackle more robust hash algorithms too, such as MD5 and SHA at the rate of 180 billion and 63 billion attempts per second respectively.
Newer 'slow hash' algorithms specifically designed to be difficult to crack using GPUs fared better against the system. Against the bcrypt hashing algorithm the system only managed 71,000 attempts per second, and 364,000 attempts per second against the sha512crypt algorithm.
According to an interview that Gosney gave to The Security Ledger, the system could be scaled up from 25 GPUs to "at least 128 AMD GPUs." This system would offer tremendous password cracking ability.
Gosney is quite adept at password cracking. Following the leaking of 6.4 million Linkedin password hashes, Gosney and a partner were able to crack almost 95 percent of the hashes.
Image source: Gosney/Passwords^12.