3.5m hosts affected by the Conficker worm globally
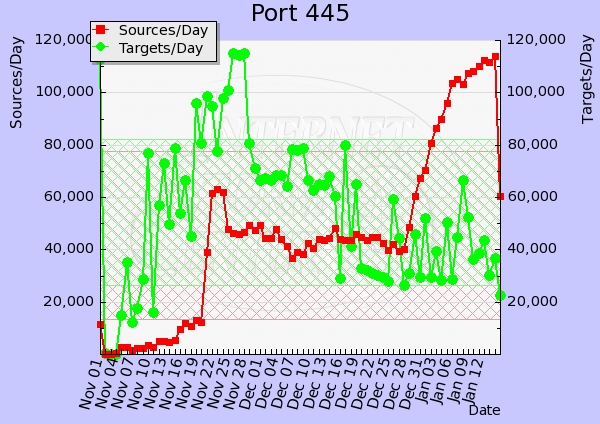
With several new Conficker variants released since the original November campaign, the worm's authors seem to be diversifying the propagation vectors in order to increase the worm's lifecycle.
Ever since the first release of the worm, the authors' criminal intentions became pretty evident. Infected hosts would be exposed to fake security software claiming that the host's security has been compromised -- appreciate the irony here -- with the worm's authors earning $30 for each and every successful sale of the bogus security software. This approach of monetizing malware infected hosts through an affiliate-based network is one of the main incentives for assembling a botnet these days.