Adobe ships insecure version of Reader from official site
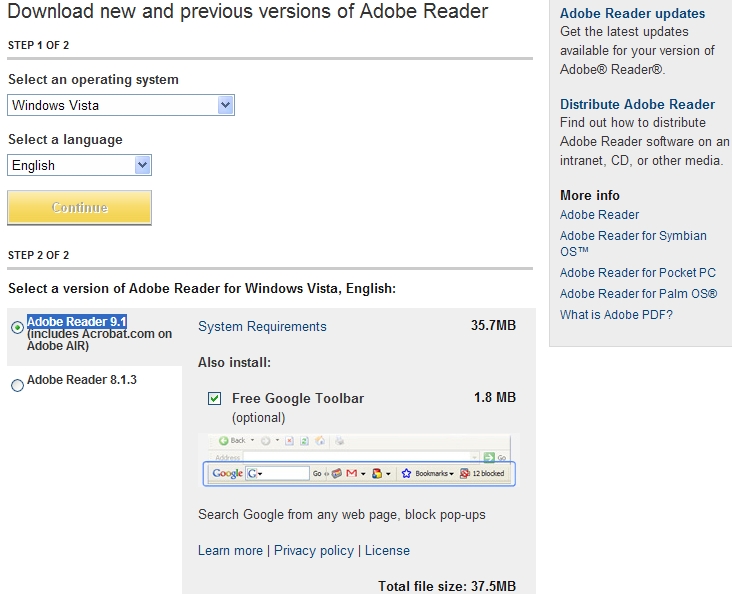
Adobe's comment on the issue:
"Adobe says the the window of vulnerability is small because its updater tries to update Reader immediately and every seven days thereafter, automatically. However, the company acknowledges that the scenario suggested by Secunia -- clicking on a malicious PDF without Reader installed -- could lead to a compromised system."
Users are always advised to download software from its official web site in order to obtain the latest version of it, and avoid the potential security implications of downloading from an untrusted third-party web site. This case clearly demonstrates something else.
Asked to comment on the issue, PSI Partner Manager, Mikkel Winther says that: "PC users need to patch! They need to patch all their vulnerable programs and they need to do so as fast as possible after the patch has been issued from the vendor. Failing to do so is playing Russian Roulette with your IT security – it is only a question of time – and luck – when your system will be compromised."
Make sure that you're in fact running the latest Adobe Reader 9.1.2, and keep in mind that cybercriminals aren't exclusively using a particular vulnerability in an attempt to infect potential victims, they're using everything there is at their disposal including historical vulnerabilities.