Android becomes second most popular malware haven in Q1

The first quarter was the most active in malware history and mobile attacks are moving to the forefront, according to McAfee data. Android attacks are also picking up.
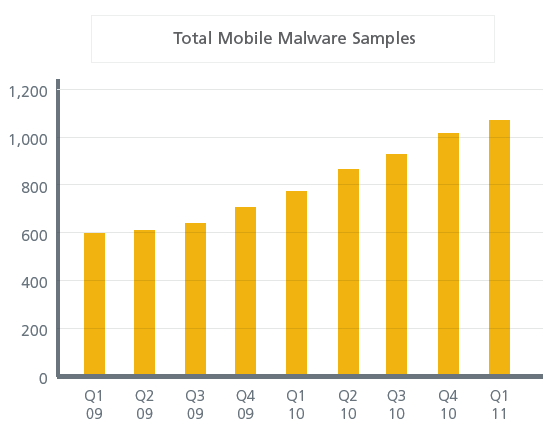
McAfee's first quarter threat report noted that attacks surged in the first quarter, but spam has fallen. In fact, there were 6 million unique malware samples in the first quarter, the highest ever for the first three months of the year. February had the most new malware samples---2.75 million.
Fake anti-virus software---think Mac Defender---reached its highest levels in march with 350,000 unique samples.
As for emerging threats, McAfee noted that Android devices are becoming malware havens. Android was the second most popular environment for mobile malware behind Symbian in the first quarter. Historically, Android remains No. 3.
Related: Malware sneaks by Google's Android Market gatekeepers again
McAfee Labs combats several developing families of malware that attack Android phones. One of the families, Android/DrdDream, comprises a variety of legitimate games and apps that have been injected with malicious code. These threats are unique and quite dangerous due to the use of two root exploits to gain greater control of those phones. The two exploits—Exploit/LVedu and Exploit/DiutesEx—were initially used by users trying to gain legitimate root access to their own devices, a process commonly referred to as rooting.1 In the PC world, malware often uses exploits to enable drive-by downloads that infect machines visiting specially designed or compromised websites. For mobile devices, much of the malware has required user interaction, but in the near future mobile exploits will certainly allow automatic malware installation. Like Android/DrdDream, the Android/Drad family is made up of maliciously modified applications.
This family sends device information to an attacker-controlled site. Just like in the PC malware world, Android/Drad listens for commands from the attacker. The malware can also download additional software, though it stops short of being a full-fledged mobile botnet. It appears that the malware uses blackhat search-engine optimization techniques, a process of manipulating search engine results to place dangerous sites higher than they should appear in lists of hits.