Android security a 'market for lemons' that leaves 87 percent vulnerable

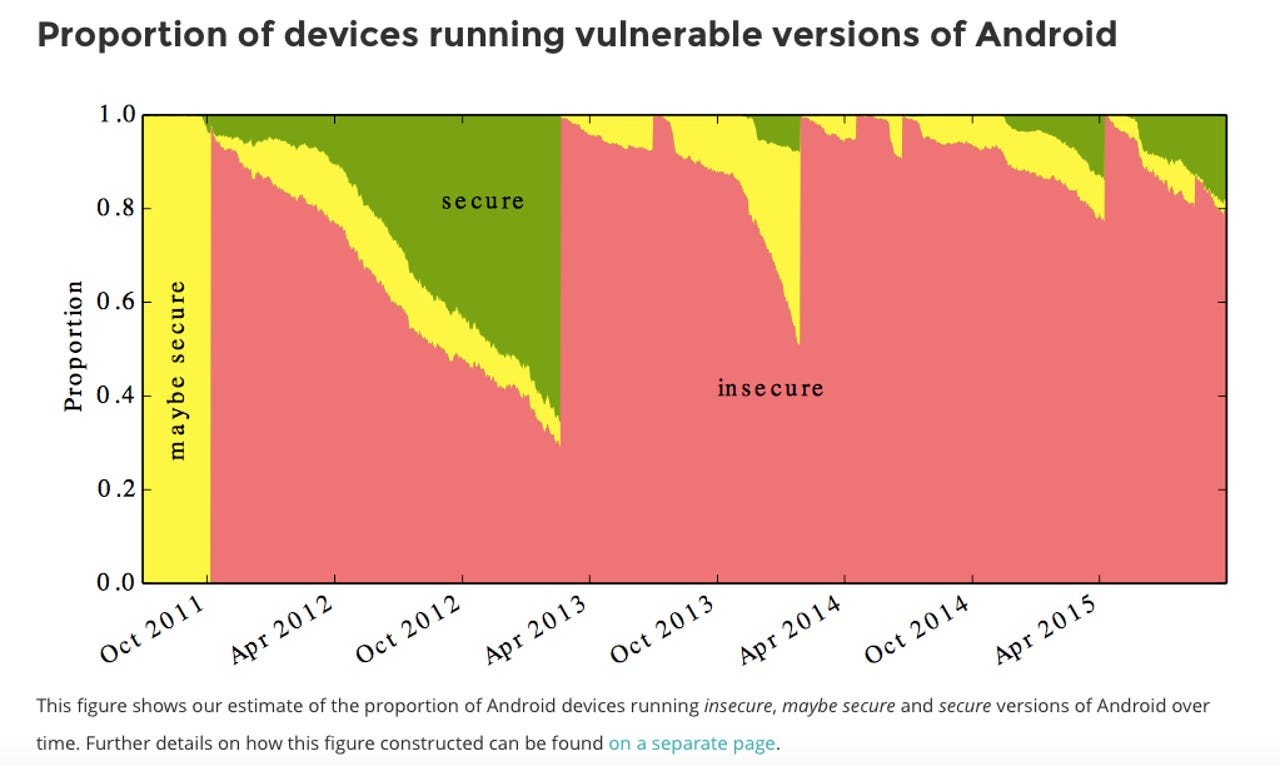
Nearly 90 percent of Android devices are exposed to at least one critical vulnerability, because of Android handset makers' failure to deliver patches, according to research from the UK's University of Cambridge.
Consumers, regulators, and corporate buyers face a common problem when assessing Android smartphones, in that no one knows which vendor will supply patches after Google develops fixes for Android security bugs.
"The difficulty is that the market for Android security today is like the market for lemons," Cambridge researchers Daniel Thomas, Alastair Beresford, and Andrew Rice note in a new paper.
"There is information asymmetry between the manufacturer, who knows whether the device is currently secure and will receive security updates, and the customer, who does not."
Their analysis of data collected from over 20,000 Android devices with the Device Analyzer app installed found that 87 percent of Android devices were vulnerable to at least one of 11 bugs in the public domain in the past five years, including the recently discovered TowelRoot issue, which Cyanogen fixed last year, and FakeID.
The researchers also found that Android devices on average receive 1.26 updates per year.
"The security community has been worried about the lack of security updates for Android devices for some time," Rice said.
"Our hope is that by quantifying the problem, we can help people when choosing a phone and that this in turn will provide an incentive for manufacturers and operators to deliver updates."
Recent alarm over a handful of Stagefright bugs has already convinced some handset makers to improve patching, with Samsung and LG committed to following Google in scheduling monthly security updates for Nexus devices.
However, HTC said monthly updates are unrealistic due to a bottleneck at the carrier testing stage, in particular for carrier-certified devices.
The researchers however noted that "the bottleneck for the delivery of updates in the Android ecosystem rests with the manufacturers, who fail to provide updates to fix critical vulnerabilities."
Nevertheless, the study is a reminder that other Android handset makers could improve patching efforts. It found that Google, LG, and Motorola far outperformed Samsung, HTC and Asus.
To illustrate patching performance, the researchers devised a 'FUM' score for each vendor, which has been published at AndroidVulnerabilities.org.
The score out of 10 comprises 'f', the proportion of devices free from known critical vulnerabilities; 'u', the proportion of devices updated to the most recent version; and 'm', the number of vulnerabilities the manufacturer has not yet fixed on any device.
Google's Nexus devices scored 5.2, followed by LG's 4.0 and Motorola's 3.1. Samsung scored 2.7, followed Sony, HTC and Asus.
Google also made software that would get a FUM score of 10
So what would FUM score would Apple get for iOS devices? And how would a handset maker score a perfect 10?
Oddly, while Android patching is a mess, another piece of software from Google would likely have a FUM score of 10. Thanks to Google's automated updates, that would be Chrome, Daniel Thomas, one of the researchers on the project, told ZDNet.
"To get a perfect 10 then new versions would need to be rolled out to 100 percent of devices within a day (to get a maximum value of u). Google Chrome can actually approach this speed at the moment so it is possible," said Thomas.
"Security updates would need to be fully deployed to all devices on the day of discovery of the vulnerability (to maximise f) and no vulnerabilities should be left unfixed for more than a day (to minimise m)."
Though the researchers don't have enough data to confidently say what Apple would score for iOS devices, it's probably only a shade ahead of Google's Nexus patching.
"I expect that iOS would get a better score than Nexus devices but I don't know by how much, it wouldn't get a perfect score," he said.
Finally, Thomas said the researchers lay blame for Android patching on vendors' shoulders rather than network operators because that's what the data suggests when comparing the speed at which new versions of Android are rolled out to a specific model relative to all device models.
"When we observe a new version [of Android] being released to a particular device model, it is deployed to most devices of that model within a month, which is much faster than the deployment rate for the whole ecosystem," explained Thomas.
"Hence, since if the manufacturer gets the update as far as the first user, it rapidly gets deployed to all users, it seems that the key bottleneck is the manufacturer producing the update. If manufacturers did a better job then I expect that the delays due to network operators and users would become the bottleneck," he added.
Still, he conceded, given the sample size, it was difficult to sift out how much of the problem lies with each entity in the patching chain, from Google, the manufacturer, network operator and user.
According to the researchers, the study was partly funded by Google.
Read more about Android
- Android, you have serious security problems
- Fretting about Stagefright on Galaxy S5? CyanogenMod's stable release has a fix
- Unpatched Android Lollipop devices open to lockscreen bypass bug