Apple QuickTime under siege

Not counting silent (undocumented) fixes, Apple has patched at least 32 security flaws affecting QuickTime in 2007. Last year, the QuickTime patch count was 28. Five were documented in 2005.
Judging by the public release of details -- and exploit code -- for zero-day flaws affecting the company's flagship media player, it looks like the number will rise again in 2008.
Take a quick peek at Milw0rm.com, a popular security research site that hosts proof-of-concept exploit code. At the moment, there are four different remote exploits for unpatched QuickTime vulnerabilities.
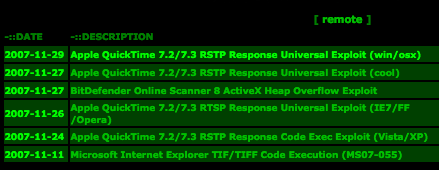
Lower down the page, there are two more proof-of-concepts for denial-of-service holes. These affect both Windows and Mac OS X users, increasing the likelihood that in-the-wild attacks against unpatched QuickTime holes will soon appear.
[ SEE: Latest QuickTime bug leaves XP, Vista vulnerable ]
The latest zero-day, a stack buffer overflow vulnerability in the way QuickTime handles the RTSP (Real Time Streaming Protocol) Content-Type header, is among the more serious flaws affecting QuickTime this year.
It affects most versions of QuickTime prior to and including 7.3 running on all supported Apple Mac OS X and Microsoft Windows platforms. Since QuickTime is a component of Apple iTunes, iTunes installations are also affected by this vulnerability.
A US-CERT advisory spells out the risks:
An attacker could exploit this vulnerability by convincing a user to access a specially crafted HTML document such as a Web page or e-mail message. The HTML document could use a variety of techniques to cause QuickTime to load a specially crafted RTSP stream. Common Web browsers, including Microsoft Internet Explorer, Mozilla Firefox, and Apple Safari can be used to pass RTSP streams to QuickTime, exploit the vulnerability, and execute arbitrary code.
This vulnerability could allow a remote, unauthenticated attacker to execute arbitrary code or commands and cause a denial-of-service condition.
The sharp rise in QuickTime flaw discoveries has set tongues wagging in security research circles and calls into question Apple's code review process.
[ SEE: QuickTime high on list of most vulnerable Windows apps ]
"QuickTime is the new IE and Apple is the new Microsoft," said a researcher who works closely with both companies on vulnerability reports.
Those comparisons aren't far-fetched. QuickTime, like Internet Explorer, is ubiquitous on Windows and often run in an unpatched state for long periods -- on both home and business computers. Apple, like Microsoft, has attracted scorn among some flaw finders for its slow response to serious issues -- and publicly documented squabbles with researchers.
Now there are calls for Apple to beef up its anti-exploitation protection mechanisms. Former Gartner analyst Rich Mogull, now an indie consultant at Securosis.com, offers the following advice:
This situation highlights why it's so important for Apple to finish some of the security improvements they started implementing in Leopard. Both library randomization and sandboxing can help prevent exploits of vulnerabilities like this. If Apple were to add outbound blocking to the application firewall, it would let us block these kinds of attacks without having to know anything about ports and protocols. Apple is clearly on the right path, and I look forward to future updates that will keep me protected even when a new, unpatched vulnerability is in the wild.
Better yet, Apple might want to (gasp!) borrow a page from Microsoft's playbook and implement an entire SDL (Security Development Lifecycle) process to cut down on flaws and reduce the attack surface when zero-days emerge.