Attacks on NFC mobile phones demonstrated
Yesterday, Collin Mulliner of the trifinite.group, a group of computer experts researching insecurities in wireless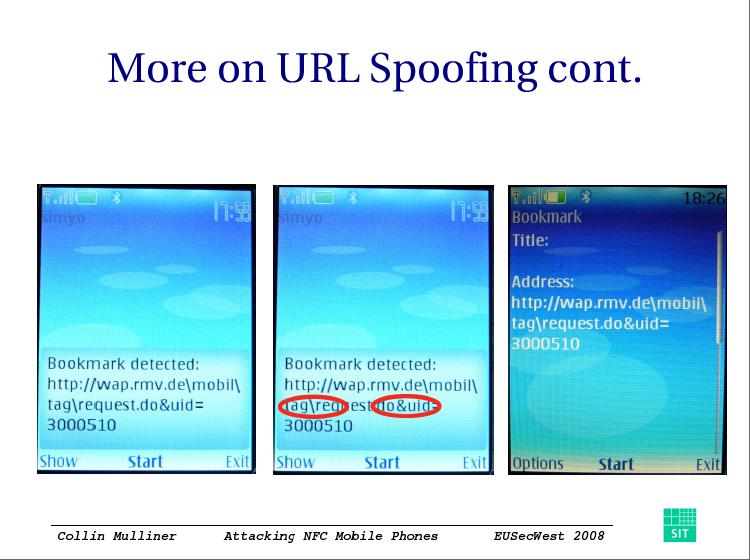
Near Field Communication (NFC) based services and mobile phones are starting to appear in the field, therefore it is time to take a look at the security of the services and especially the NFC mobile phones them self's. The presentation will provide this first look at the security of NFC mobile phones. We will show some known theoretical attacks and how they may work in the field. Further we will present results from analyzing a specific NFC mobile phone, here we will reveal some security issues and methods to exploit them. Also we will provide a small survey of NFC applications in the field. Finally we will release a small set of tools to do further analysis on NFC mobile phones and applications.
We recognize that NFC is not widely used yet but we anticipate that it will be in the near future due to the massive effort carried out by the member companies (http://www.nfc-forum.org/member_companies/). Also since NFC is based on RFID technology (ISO 14443) the whole topic should be highly interesting for wide range of security professionals and researchers. The innovative part of this presentation is that it is the first presentation on this topic and it shows mainly real world attacks and provides some hands-on experience for the security people and application developers.
The attacks demonstrated are trivial due to the manufacturer time to market (TTM) obsession, thereby shipping devices with trivial vulnerabilities, in Mulliner's research they orbit around passive tags which are mostly abused as vectors for the any of the attacks demonstrated. What about the market's acceptance of the technology?
Mastercard has just announced that it's starting a mobile contactless payment pilot across Canada, citing interesting survey results that a malware author or a phisher would definitely enjoy :
Interest in it isn't raging yet, according to IDC Canada's vice-president of communications and segments Tony Olvet. He cited a 2007 survey of 541 15-to-29-year-olds, where 8.8 per cent of them said they would be interested in contactless payments via cell phone. He said that, once visibility of these technologies increases with the PayPass and PayWave trials and rollout, interest will most likely rise.
Let interest rise proportionally with the shipped pre-audited devices, where security and awareness on the potential threats isn't sacrificed for achieving your TTM objective.