Beware this Android banking malware posing as a software update

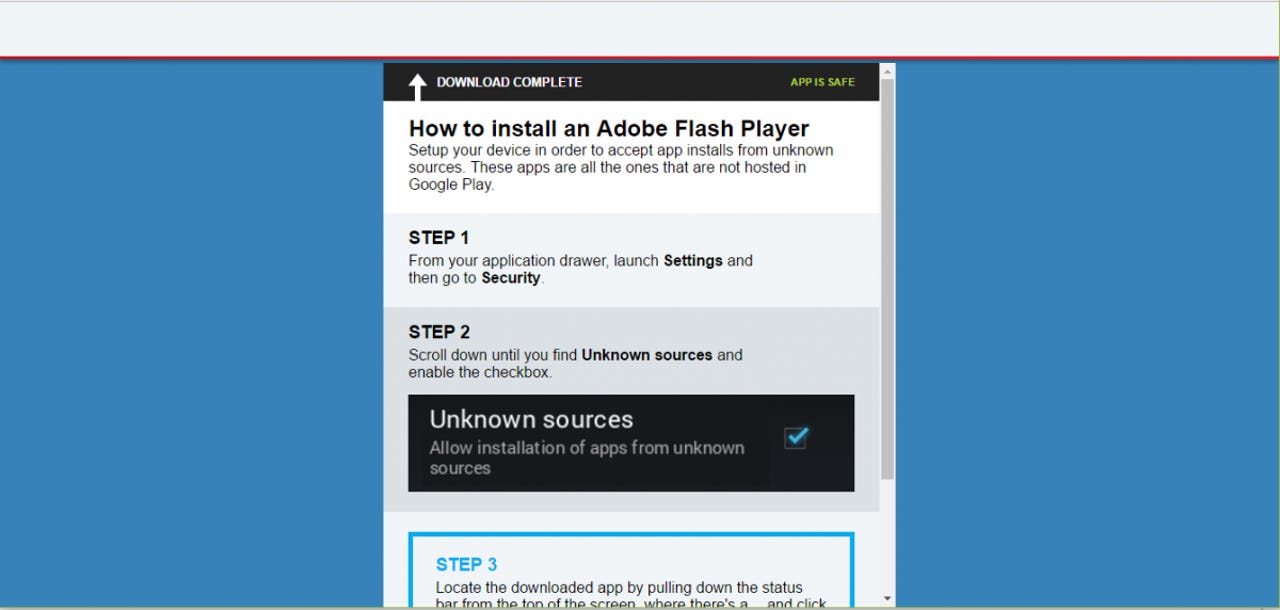
The malware provides a step by step guide to disabling security features so it can do its nefarious bidding.
A sophisticated banking trojan has once again develop new techniques in order to trick Android users into downloading the malware.
It's the latest variant of Marcher Android malware and this time it's posing as an Adobe Flash Player Update. Having first appeared on Russian-speaking undeground forums in late 2013, previous incarnations of Marcher have posed as a security update a Super Mario mobile game and more.
Uncovered by researchers at Zscaler Threatlabz, this version of the banking trojan is using new lure techniques to spread infections, including adult content and links taking advantage of hype around new mobile games. All of the malware downloads are accessed from third-party sites and not via the official Google Play store.
Once the victim has opened the dropper URL, they'll be prompted with a message saying the device's Flash Player is out of date and needs updating. Of course, this is fake, but if the user goes through and downloads the playload, they'll become infected.
Marcher even offers a step by step guide on how to disable security settings and allow the device to install third-party software - an option turned off by default on Android devices and a key way of protecting the user from malicious software.
Once installed, the malware will immediately hide itself and remove its icon from the phone menu, and register the infected device with its command and control server. All of the meta information about the infected phone, including the installed apps list is sent to the C&C server.
The malware lies in wait for the user to open one of its targeted apps, but instead of the official, authentic login page, Marcher displays a fake overlay, allowing the cybercriminals behind it to steal login credentials and gain access to bank accounts and email services.
Some of the apps Marcher provides fake login pages for include Citibank, TD Bank, PayPal, Gmail, Facebook, Walmart, Amazon, Western Union and more. The list of targets is in fact hardcoded into the malware payload, but the fake login pages can be changed by the authors as and when needed.
Apps and websites targeted by Marcher malware.
Researchers note that unlike previous versions of Marcher, this variant is highly obfuscated, allowing it to bypass most antivirus programmes. Indeed, VirusTotal shows that it's caught under 20 percent of the time by virus scanners.
"We have been seeing regular infection attempts for this Marcher variant in the past month. The frequent changes in the Marcher family indicate that the malware remains an active and prevalent threat to Android devices," said Viral Gandhi, senior security researcher at Zscaler.
In order to avoid infection via Marcher and over Android malware which spreads itself from third-party websites, users should only download apps from trusted app stores such as Google Play - although the official Android market still doesn't keep malicious software out one hundred percent of the time.
READ MORE ON CYBERCRIME
- This sneaky mobile malware just evolved into something even nastier
- Android alert: This cutesy malware has infected millions of devices
- This is the easiest way to prevent malware on your Android device [CNET]
- FalseGuide malware dupes 600,000 Android users into joining botnet
- How cybercriminals are using Android security bulletins to plan attacks [TechRepublic]