Do not touch this one Android setting and most malware will leave you alone, mostly

If you love to traverse the web and install random apps from weird and shady parts of the internet, of course you're going to have a bad time. This is accepted wisdom in the Windows world, and so it should be in the mobile world, too.
Make no mistake, Android has massive fundamental security issues to tackle, and there are millions of hostile apps looking for every opportunity to empty your bank accounts, or use devices as spam relays, or cryto-ransom and lock a phone until you hand over your hard-earned, or just sit there lurking and waiting for the moment a commmand-and-control server tells them to turn evil.
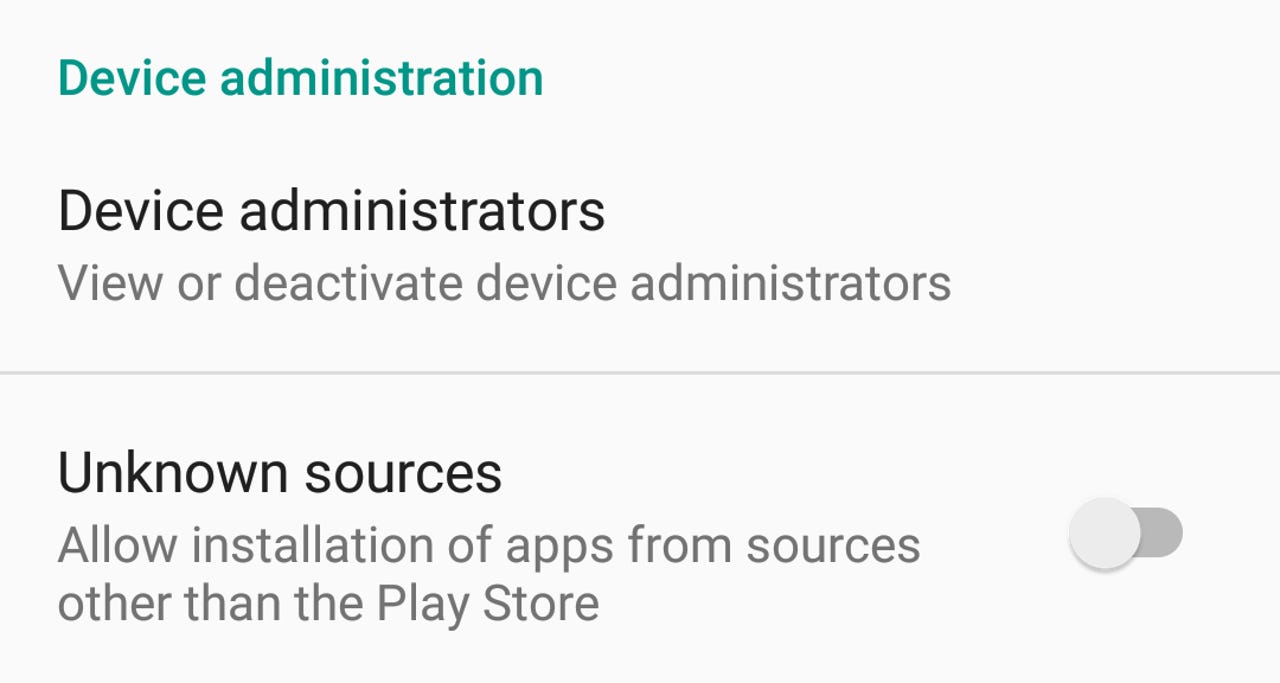
Against this toxic cesspit of threats, it is surprisingly simple to eliminate a great many potential threats, and that is not allow an Android device to install apps from anywhere else other than the Google Play Store.
This takes the form of the Unknown Sources option in modern Android releases.
A particularly nasty trojan masquerading as a Flash Player update that looked to steal credentials from Australian, New Zealand, and Turkish banking customers appeared recently, and set off the usual Android malware hype cycle.
However, there were two important hurdles that this trojan had to clear before it could get to work: Convince the user to allow installation of an untrusted app of unknown origin, and then gain Device Administrator status on the device. It's a process that would involve at least one, potentially two, warning dialogs depending on the status of the Unknown Sources setting.
It's a common footnote to many mobile malware discoveries, be it Android or iOS, that a very destructive piece of malware is found, and then buried in the details is that the device is rooted, or the app is sideloaded.
In its Android Security 2014 Year in Review [PDF], Google said allowing non-Play apps to be installed on Android made users seven times more vulnerable to malware.
"Worldwide, excluding non-malicious rooting applications, PHAs [potentially harmful apps] are installed on less than 0.1 percent of devices that install applications only from Google Play. Non-rooting PHAs are installed on approximately 0.7 percent of devices that are configured to permit installation from outside of Google Play."
Google said it does over 200 million security scans of devices per day.
Simply not allowing non-Play Store install is far from a panacea, as Google's continuing issues with unsuccessfully putting Stagefright behind them shows.
Security
Malware, on any device, is much more likely to find its way onto devices through the good, old fashioned technique of tricking the users into self-harm. As the ProofpointThe Human Factor Report [PDF] said, humans are often the weakest link.
"By an overwhelming margin, attackers infected computers by tricking people into doing it themselves, not through automated exploits," it said. "98 percent of URLs in malicious messages link to hosted malware ... to work, these files have to be opened by the user. So attackers trick users into double-clicking them and infecting themselves."
These results also apply to Android users, as Kaspersky said last month when it spoke about the Acecard banking trojan.
"Mobile devices were usually infected after downloading a malicious application masquerading as a legitimate one. Acecard versions are typically distributed as Flash Player or PornoVideo, although other names are sometimes used in a bid to imitate useful and popular software," it said.
However, at the end of last year, Kaspersky found something disturbing.
"On 28 December 2015, Kaspersky Lab experts were able to spot a version of the Acecard downloader Trojan - Trojan-Downloader.AndroidOS.Acecard.b - in the official Google Play store. The Trojan propagates under the guise of a game. When the malware is installed from Google Play, the user will only see an Adobe Flash Player icon on the desktop screen and no actual sign of the installed application."
So while it is far from infallible, and undesired behaviour and malware infections do happen if you do the safe thing and allow only apps to install from Play Store -- as Gmobi and the FTC showed last week -- it is possible to avoid much of the muck and fear that is peddled when it comes to using Android.
If there was an option to lower your chances of catching the flu by seven times to 0.1 percent, you'd take it, and so the same should be applied to mobile.
ZDNet's Monday Morning Opener is our opening salvo for the week in tech. As a global site, this editorial publishes on Monday at 8am AEST in Sydney, Australia, which is 6pm Eastern Time on Sunday in the US. It is written by a member of ZDNet's global editorial board, which is comprised of our lead editors across Asia, Australia, Europe, and the US.
Previously on the Monday Morning Opener:
- How Apple became Samsung, and why Steve might have approved
- Open Compute Project: Gauging its influence in data center, cloud computing infrastructure
- VR is the next big thing, whether you can see it or not
- For simplicity and security, Apple needs to draw a line now to prevent further ones
- Will Galaxy S7 keep Samsung in pole position?
- A call for more cloud computing transparency
- Microsoft and mobile: The headache that won't go away
- If a smartphone vendor acquiesces to anti-encryption laws, don't use them