Can you trust that invoice? Nigerian 419 scammers ply new wire-wire trade via compromised email

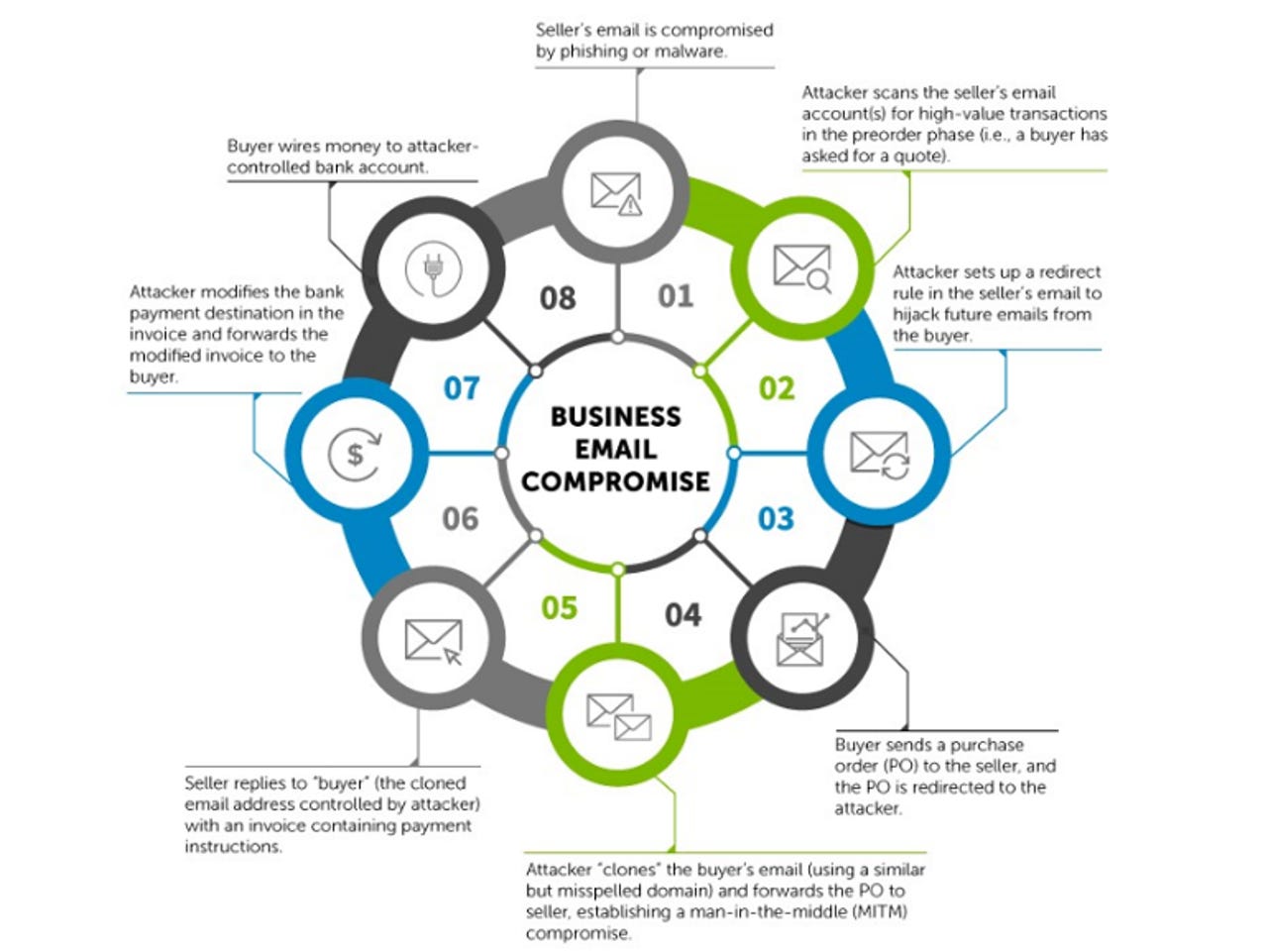
These are the eight stages involved in a typical wire-wire business-email compromise attack.
Former Nigerian 419 scammers are turning to more sophisticated and bigger-paying jobs that start with compromising the email accounts of company staff responsible for selling, and then waiting for a juicy request for a quote.
According to Dell SecureWorks, these new-generation Nigerian scammers are known as 'waya-waya' (or wire-wire) and conduct wire fraud by compromising a supplier's email.
The FBI warned earlier this year that businesses have been exposed to an estimated $3.1bn in potential losses due to so-called business email compromise (BEC) scams since 2013. These crimes usually take the form of an attacker spoofing the email account of a CEO and then ordering a subordinate to transfer funds to a supposed supplier's account.
However, SecureWorks' says its probe into one Nigerian operation uncovered a far more "devious" attack than spoofing the boss' email account. The attackers instead are compromising a seller's email account to place themselves between the buyer and seller during a transaction.
The tools the Nigerian scammers are using are not sophisticated and include cheap phishing kits and commodity malware that log keystrokes and take screenshots. However, they're also targeting businesses that have equally unsophisticated security and lax processes for international wire transfers.
Once the attacker has access to the seller's email account, they simply monitor the account for a lucrative transaction.
This monitoring is carried out by setting an auto-forward rule on the compromised email account, which delivers all email from the buyer to the attacker's account. The key document the attacker is looking to capture is the purchase order from the buyer.
The attacker then sets up a bogus email account that looks like the buyer's real email address, and forwards the purchase order to the seller, inserting themselves in the middle of the transaction. The seller then sends an invoice, which contains payment instructions, to the account they believe is the buyer's.
"When it is time for payment details to be relayed to the buyer via an invoice, the threat actor intercepts the seller's email and changes the destination bank account for the buyer's payment. If the payment account does not appear to be suspicious, the buyer will likely submit the payment to the attacker's account," SecureWorks explained.
According to the company, one unnamed US chemical company that fell for this exact scam unwittingly wired $400,000 to a Nigerian attacker's account when attempting to purchase goods from an India-based chemicals supplier.
In that instance, the Indian firm's web application for corporate email had been compromised. The firm notably did not have two-factor authentication enabled.
SecureWorks has dubbed the group, which has 30 members, Wire-Wire Group 1 (WWG1). It gained access to the group after one of its members infected his own machine with malware and started uploading screenshots and keystroke logs to an open directory on a web server.
Based on an analysis of invoices and purchase orders captured from the server, SecureWorks believes the group steals about $3m a year from companies, although losses to businesses may be as high as $6m.
More on security
- Windows 10 Edge: Now Microsoft puts $15k bounty on remote attack browser bugs
- 10 tips for spotting a phishing email (TechRepublic)
- Hackers target Queensland premier's department
- With its bug bounty, Apple shows it finally finds hackers useful
- This ATM hack could allow thieves to make off with thousands
- Meet the 'average paperclip threat': Why Airbnb rentals are the next big attack surface
- How hackers used this Trojan malware to spy on a territorial dispute
- How to access Tor, even when your country says you can't
- Snapchat worker falls for email phishing scam (CNET)