Chinese APT group Naikon targeted Western Australia government

Check Point Software Technologies' threat intelligence arm has uncovered a Chinese APT group is targeting several governments in the Asia Pacific region, including the government of Western Australia.
Check Point Research said the five-year, ongoing cyber espionage operations of Naikon targeted governments within Australia, Indonesia, Philippines, Vietnam, Thailand, Myanmar, and Brunei through "government-to-government" attacks.
According to the IT security firm, Naikon's primary method of attack is to infiltrate a government body, then use that body's contacts, documents, and data to launch targeted phishing attacks against other government targets, thereby exploiting the trust and diplomatic relations between departments and governments to increase the chances of its attack succeeding.
Through the use of a backdoor named Aria-body, Naikon gained remote access to the infected PC or network and bypassed security measures. With such access, the group could copy, delete, or create files.
Although Naikon was active in 2015 before slipping from the public eye, Aria-body has been observed to have developed new ways of avoiding detection, with the researchers saying this proves the group has accelerated its cyber espionage activities in 2019 and Q1 2020.
In a report released this week, Check Point revealed its investigation had kicked off after it observed a malicious email that was sent from a government embassy in APAC to an Australian government entity, named The Indians Way.doc.
Check Point confirmed with ZDNet this was the government of Western Australia.
"This RTF file, which was infected (weaponized) with the RoyalRoad exploit builder, drops a loader named intel.wll into the target PC's Word startup folder. The loader in turn tries to download and execute the next stage payload from spool.jtjewifyn[.]com," Check Point said.
See also: 12 years on, audit finds WA government entities still don't get infosec
Aria-body starts with gathering data on the victim's machine, including: Host-name, computer-name, username, domain name, windows version, processor ~MHz, MachineGuid, 64bit or not, and public IP.
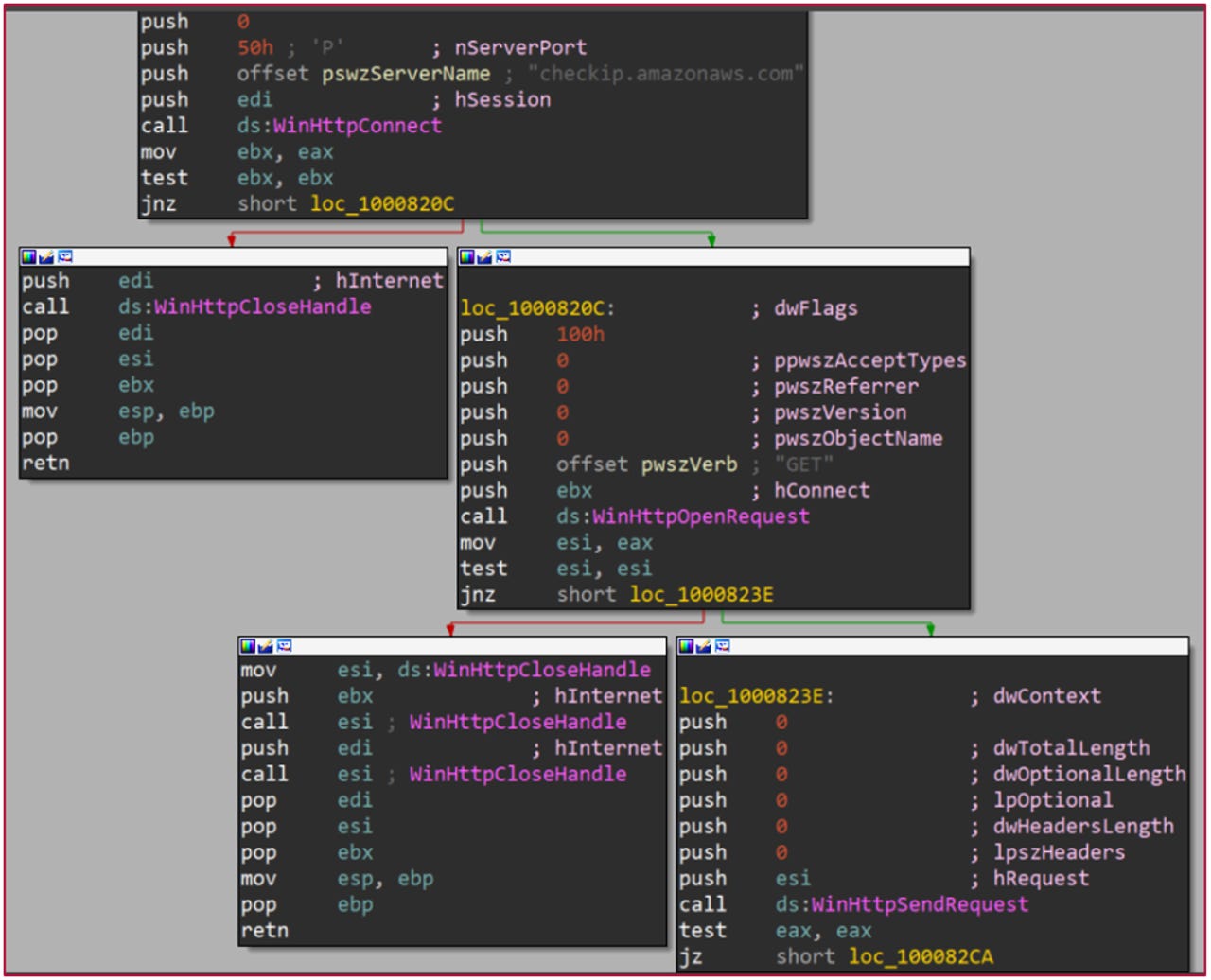
Aria-body using checkip.amazonaws.com service to get victim's IP
Check Point said Naikon specifically targets government ministries of foreign affairs, science, and technology, as well as government-owned companies. It said the motive is believed to be the gathering of geo-political intelligence.
"What drives them is their desire to gather intelligence and spy on countries, and they have spent the past five years quietly developing their skills and introducing a new cyber-weapon with the Aria-body backdoor," manager of threat intelligence at Check Point Lotem Finkelsteen said.
"To evade detection, they were using exploits attributed to lots of APT groups, and uniquely using their victims' servers as command and control centers. We've published this research as a warning and resource for any government entity to better spot Naikon's or other hacker group's activities."
LATEST SECURITY NEWS
- For 8 years, a hacker operated a massive IoT botnet just to download Anime videos
- This phishing campaign targets executives with fake emails from their phone provider
- A hacker group tried to hijack 900,000 WordPress sites over the last week
- Security warning: State-backed hackers are trying to steal coronavirus research
- Australia progressing work on agreed norms of responsible state behaviour in cyberspace