Cyber-security firm Verint hit by ransomware

The Israel offices of US cyber-security firm Verint have been hit by ransomware, according to a screenshot taken by a Verint employee that started circulating online earlier today.
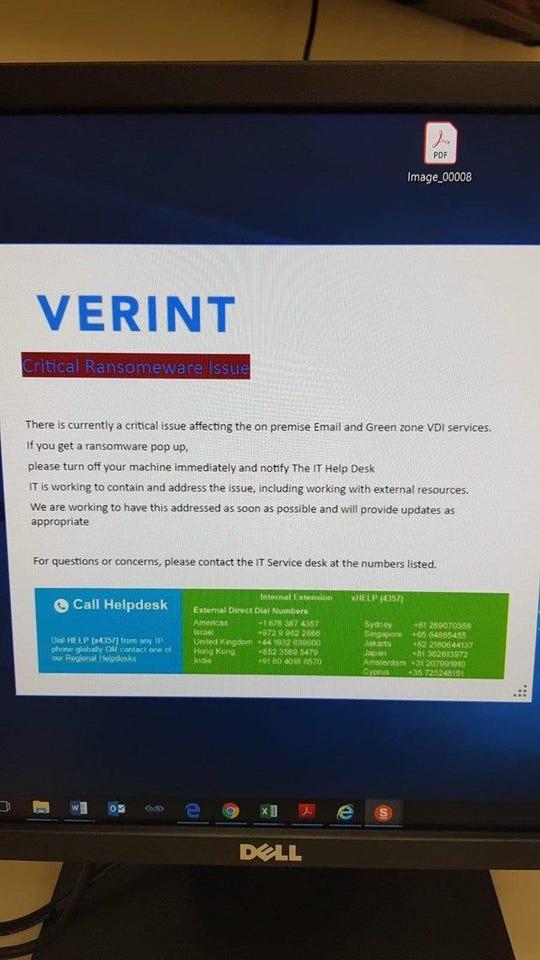
"There is currently a critical issue affecting the on premise Email and Green zone VDI [Virtual Desktop Infrastructure] services," read a warning message that was displayed earlier today on Verint employees' computers.
"If you get a ransomware pop up, please turn off your machine immediately and notify The IT Help Desk. IT is working to contain and address the issue, including working with external resources.
"We are working to have this addressed as soon as possible and will provide updates as appropriate," the internal warning message read.
Multiple sources have told ZDNet the incident is real, and that FireEye's Mandiant incident response team is on-premise to help with recovery efforts.
Verint confirmed the incident to Israeli news sites TheMarker, Calcalist, and Globes. "The company's defense system identified the attack immediately after it began," a Verint spokesperson said, "and carried out the activity required to thwart it."
The company did not respond to additional requests for comment from ZDNet.
Verint was founded in 1999 and sells analytics, security, surveillance, and business intelligence services. While the company is US-based, it does most of its business from Israel.
Many of 2018's most dangerous Android and iOS security flaws still threaten your mobile security
Related malware and cybercrime coverage:
- Malvertising campaign abuses Chrome for iOS bug to target iPhone users
- The Bayrob malware gang's rise and fall
- Reveton ransomware distributor sentenced to six years in prison in the UK
- Scranos rootkit expands operations from China to the rest of the world
- Emotet hijacks email conversation threads to insert links to malware
- US government publishes details on North Korea's HOPLIGHT malware
- How the United Nations helps fight global cybercrime TechRepublic
- Apple removed popular app that was secretly stealing your browser history CNET