Cyberattacks on US jump to 77,000 but patching efforts cut down vulnerabilities

The total number of incidents that agencies reported in 2015 is up 10 percent from 2014.
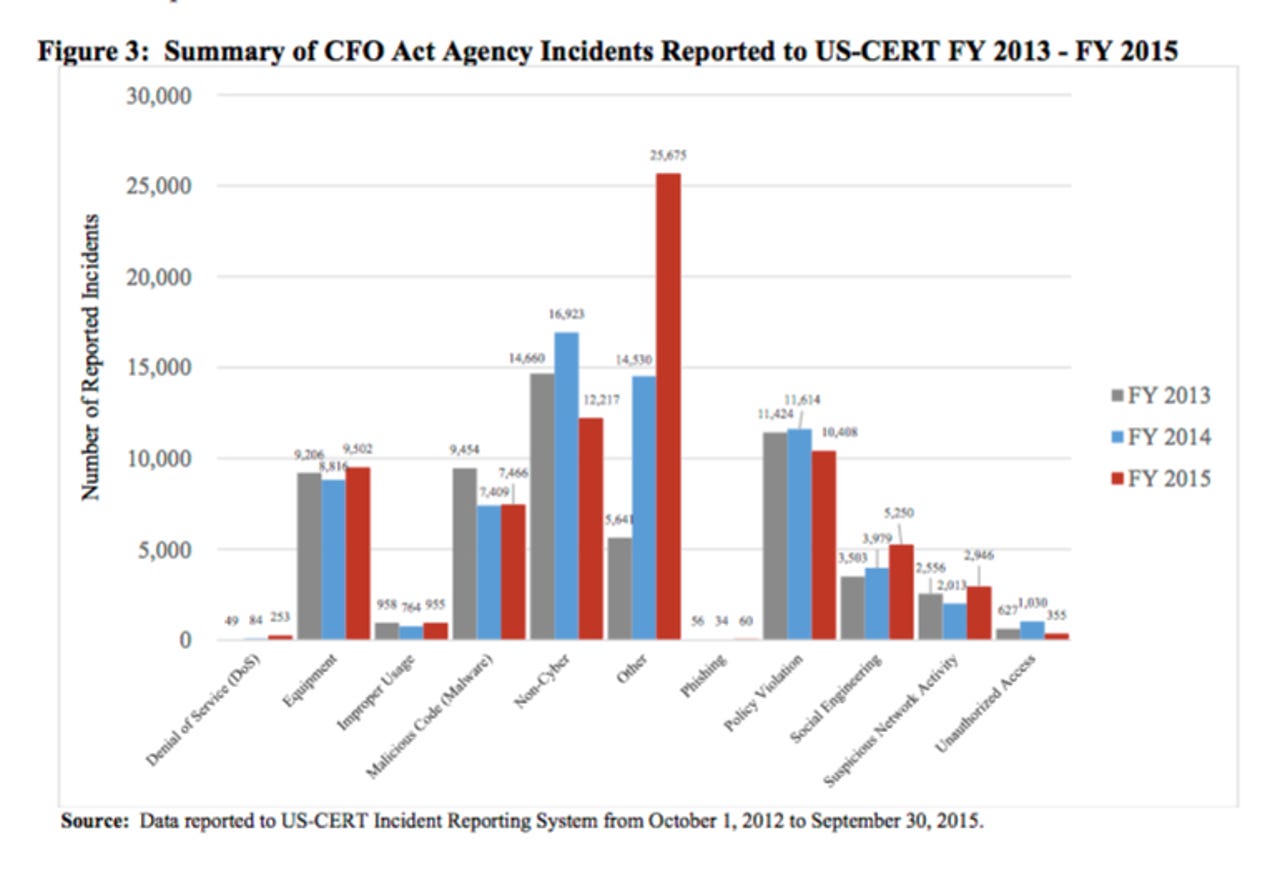
US federal agencies reported 77,183 cyber incidents in 2015, the Office of Management and Budget (OMB) says in a new report.
The number of incidents that agencies reported last year to the Department of Homeland Security's (DHS) US Computer Emergency Readiness Team (US-CERT) shows an increase of 10 percent compared with 2014, according to OMB's Federal Information Security Management Act (FISMA) report.
"The overall rise in the number of incidents represents both an increase in total information security events and agencies' enhanced capabilities to identify, detect, manage, respond to, and recover from these incidents," OMB said.
The incidents include denial of service, improper usage -- such as unauthorised access, phishing, and policy violation -- malware, non-cyber breaches such as leaked printed material, and suspicious network activity detected by EINSTEIN, the federal government's early-warning system, otherwise known as the National Cybersecurity Protection System.
By far the largest number of incidents fall into a category called 'Other', which includes "low-frequency types of incident reports, such as unconfirmed third-party notifications, failed brute-force attempts, port scans, or reported incidents where the cause is unknown".
These incidents account for 34 percent of the total, amounting to 25,675 incidents for the year, and are up by 77 percent on 2014.
"Approximately 59 percent of 'Other' incidents fall within the attempted access subcategory due to the high volume of scans and probes," OMB reported.
Suspicious network-activity incidents, which are primarily derived from EINSTEIN, total 2,946 in 2015, down from 2,013 in 2014.
The number of phishing incidents reported is less than 50 for 2015. OMB notes the reported figures "do not capture the magnitude" of phishing attacks. The reason for such low figures is that US-CERT categorizes phishing incidents based on root cause, such as malware or social engineering.
The OMB said the government has successfully cut down the number of "active critical vulnerabilities" on federal systems from 363 known critical bugs in May to just three by December, amounting to a 99 percent reduction in seven months.
The huge reduction in vulnerabilities is the result of the DHS National Cybersecurity and Communications Integration Center (NCCIC) running "persistent network and vulnerability scans of all federal civilian agency internet-accessible systems".
On May 21, in the wake of the massive OPM hack, the DHS issued a Binding Operational Directive requiring all agencies to patch vulnerabilities within 30 days of receiving the NCCIC report or else explain why they can't and outline steps to resolve the issue.
According to the OMB, DHS says it has now pushed forward its timeline for delivering EINSTEIN 3, the latest phase of the system, across the government from 2018 to 2016.
Currently the system provides services to 49 percent of the government's civilian user base, representing 1.1 million users.
The US Government Accountability Office (GAO) criticized EINSTEIN for "not fully" meeting its stated objectives.