Cybercrime market selling full digital fingerprints of over 60,000 users

Today, at the Kaspersky Security Analyst Summit conference taking place in Singapore, security researchers from Kaspersky Lab have revealed the existence of a new cybercrime marketplace where crooks are selling full digital fingerprints for over 60,000 users.
This new marketplace is like nothing that has ever been seen on the hacking scene until now.
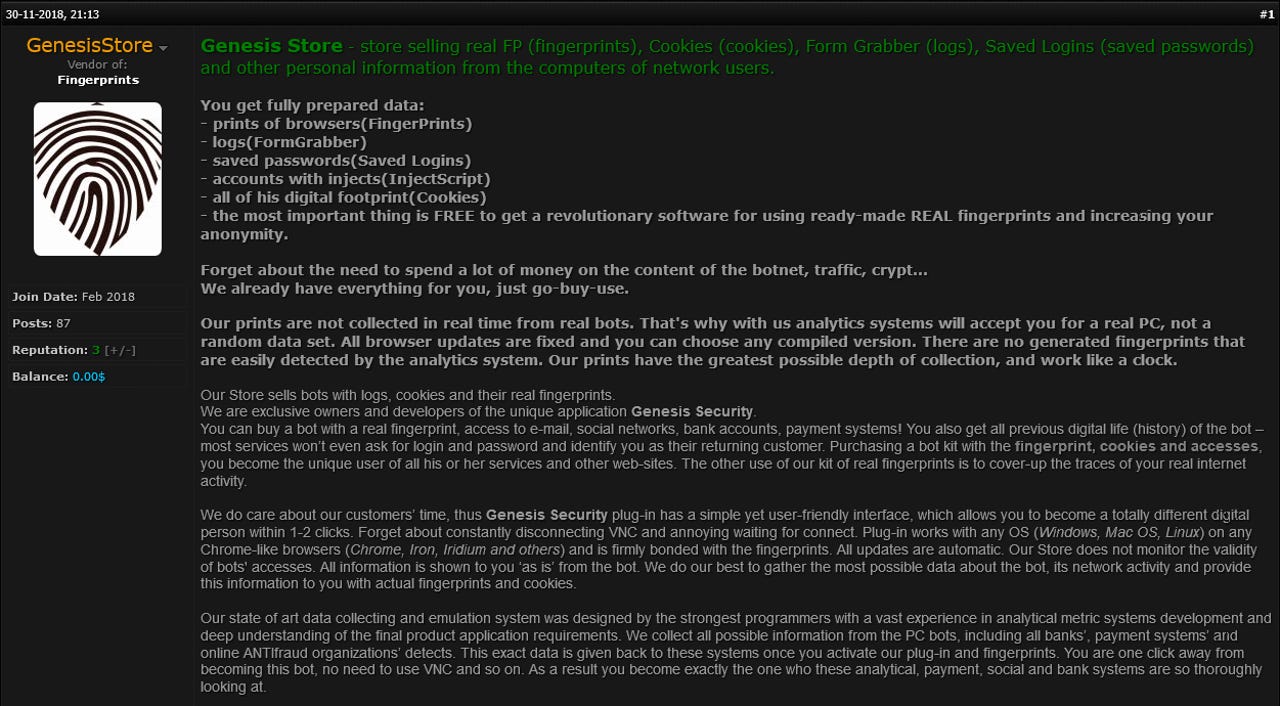
Named Genesis, the service launched in the fall of 2018, when its creators began advertising it as a "secondary/related service" on several carding forums (forums where cyber-criminals sell stolen payment card details).
Genesis' main product is users' full digital profiles.
Users who in the past have been infected with malware or who have installed rogue browser extensions have unknowingly had their account passwords and full browser details recorded, and then sent to Genesis operators.
Each user profile includes login credentials for accounts on online payment portals, e-banking services, file-sharing or social networking services, but also the cookies associated with those accounts, browser user-agent details, WebGL signatures, HTML5 canvas fingerints, and other browser and PC details.
Genesis operators make their profits by selling this information on their marketplace to other cyber-criminal groups. The marketplace's main clientele are cyber-criminal engaged in online fraud, identity theft, and money mule operations.
Genesis buyers can acquire a user's digital identity for prices ranging from $5 to $200 and then log into that user's account to steal funds, personal photos, sensitive or proprietary documents, or submit official papers on his behalf (to government-related agencies).
To use any of the user identities crooks buy from Genesis, buyers will have to install a Chrome extension that has been created by the Genesis team.
This extension, provided free of charge to any buyer, automatically imports and applies a Genesis-bought identity, transforming the buyer's browser into a near-identical clone of the real user's browser.
The reason why a marketplace like Genesis has come to exist today is because in recent years, online services have improved their anti-fraud systems, and are now capable of detecting abnormal account login activity by looking at more details, rather than only a user's username and password.
Genesis identities (also called masks or fingerprints) will allow a crook to look as close to the real account owner as possible, fooling some of these modern anti-fraud systems, often deployed with online payment and e-banking services.
In an online ad found by ZDNet, Genesis' creators claim they "reviewed top 47 analytical systems and 283 major banks and payment systems" in order to determine what tracking and detection systems their cloned fingerprints needed to bypass.
Kaspersky said today that Genesis has already entered the arsenal of some cyber-criminal gangs, and they are "actively using such digital doppelgangers to bypass advanced anti-fraud measures."
Experts recommend that users enable multing-factor authentication for every online account that supports it, but also recommend that companies add support for additional user identification mechanisms, such as biometrics.
A basic guide to diving in to the dark web
Related malware and cybercrime coverage:
- Over 58,000 Android users had stalkerware installed on their phones last year
- TrickBot Trojan seeks out weak human links in business to profit from the tax season
- IoT botnet targeting your enterprise? Nope. Just a kid with an ExploitDB account
- Security researchers discover iOS version of Exodus Android spyware
- Cybercrime group FIN6 evolves from POS malware to ransomware
- Hacker group has been hijacking DNS traffic on D-Link routers for three months
- How the United Nations helps fight global cybercrime TechRepublic
- Apple removed popular app that was secretly stealing your browser history CNET