D-Link router's CAPTCHA flawed, WPA passphrase retrieved
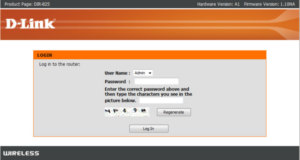
According to SourceSec, the flawed implementation allows an attacker/malware to retrieve the router's WPA passphrase with user-level access only, and without even a properly solved CAPTCHA. Moreover, a combination of a simple Javascript code using anti-DNS pinning doesn't even require the attacker to have malware installed on the router, instead, the attack can be triggered by visiting a web site.
- Malware loads the router’s index page and glean the salt generated by the router
- The malware uses the salt to generate a login hash for the D-Link User account (blank password by default)
- The malware sends the hash to the post_login.xml page
- The malware sends a request to the wifisc_add_sta.xml page, activating WPS
- The attacker uses WPSpy to detect when the victim’s router is looking for WPS clients, and connects to the WiFi network using a WPS-capable network card
Ironically, the first router with CAPTCHA implementation can in fact be undermining the secure combination of strong passphrases and strong encryption protocols, which of course doesn't mean that these best practices are in wide circulation at places they're supposed to be.