Email security has been around forever, you just need to turn it on

This information is also available as a TechRepublic download.
As much as I respect my colleague and mentor David Berlind who taught me the news business, I have to say that he's got it all wrong when it comes to Internet mail security. Berlind is reeling over his incorrect perception that the Internet still lacks secure email. The problem is that he's got it all wrong and the solution has been under his nose all this time and it really isn't the non-interoperable nightmare he paints it to be. Secure connections between Server to Client, end to end, and Server to Server communications have all been around for a long time. The technology is already baked in to existing software and it's simply a matter of installing, configuring, or merely enabling the technology. [Update 7/26/2007 - Berlind follows up here. I respond here. Awesome and informative response from Ani Shrotri]
Server to Client encryption is a check mark away: The most likely way to get eavesdropped on is in the last 100 feet whether that's through a wire (through layer 2 hijacking) or wireless LAN connection. To enable Server to Client encryption, you simply check a simple option to enable SSL and type a different port number for your POP3 (inbound) and SMTP (outbound) Mail Server settings in your email client. My current DSL provider AT&T like most ISPs supports SSL encryption on POP3 and SMTP and it's as simple as a checkmark and using ports 995 for POP3 and 465 for SMTP instead of the usual ports 110 and 25. The problem is that AT&T doesn't disable unencrypted mode which means the vast majority of users won't use the secure transport mode.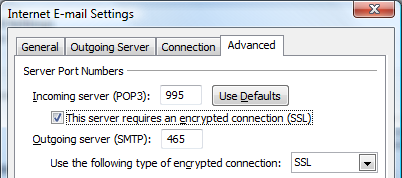
If you happen to be a Gmail kind of guy or gal, simply typing in https://mail.google.com (not http://) and your entire authentication and web mail session is encrypted with export-restricted grade SSL encryption. The problem with Google (similar to AT&T not disabling regular POP3 and SMTP) is that they don't disable http mode which means 99% of the population will continue using unencrypted http mode. Hotmail doesn't support payload encryption so Hotmail users out of luck (are you listening Microsoft?).
End to End email cryptography: End to end cryptography which encompasses authentication, non-repudiation, and encryption has been baked in to every email client in the form of S/MIME for a decade with push button simplicity and full interoperability. In fact an email client without S/MIME support is like a web browser that doesn't support HTTPS SSL mode. All you need to do is obtain a FREE Personal Digital Certificate from a Certificate Authority like Thawte through a web enrollment process. In that enrollment process, you get to generate your own Public and Private Key pair and Thawte will digitally sign your Public Key after and email round trip where you demonstrate control and possession of your email account.
Once you've obtained that Certificate, you can digitally sign any email and everyone in the whole world using an email client less than a decade old will be able to read and trust that digital signature to have truly come from the purported "from" email address. The other side doesn't even need their own Digital Certificates to read your signatures. This is the "authentication" component.
Note that I said they can trust that it came from the purported email address and I didn't say the digital signature proves the message came from you. If you want to prove it came from you, you're going to have to go to the WOT (Web Of Trust) and get someone acting as a Thawte Notary to bind your identity to your email address and Digital Certificate. With your identity bound to your email and Digital Certificate, you now have non-repudiation and your signed emails can be treated as contracts under the eyes of the law. Non-repudiation means that when you send out a message with your digital signature bound to your email and identity, you cannot claim anyone else falsified that message because only the owner of your private key could have generated that digital signature.
To enable encryption, both sides must have their own Digital Certificate which also means both sides can digitally sign. Once the Digital Certificates are installed on each end, you simply need to click the "encrypt" button built in to your email client. The beauty of this encryption scheme is that it doesn't care if the network and server infrastructure in the middle is trusted or not because only the end points can decrypt the messages. This however does not negate the need for Server to Client encryption because we don't want someone else to be able to take over the email account on either end even if they can't read the encrypted messages.
S/MIME is so universal that even companies like PGP Corporation which offer solutions that manage an Enterprise's cryptography infrastructure will support technologies like S/MIME in addition to PGP and GPG. PGP and GPG are alternatives to S/MIME but the technology isn't baked in every email client and must be installed as an add-on.
Server to Server cryptography: Sniffing traffic between two SMTP servers is REALLY difficult to pull off unless you have access to the ISP's (Internet Service Provider) infrastructure, or you've hacked in to a server on one end, or you've hacked a router or firewall between the company and the ISP. In fact if you could hijack someone's email server, you can actually steal their domain name or obtain SSL certificates on behalf of the actual owner. But we can mitigate these types of attacks by enabling Server to Server encryption even if a hacker manages to place themselves between your server and the Internet. Enabling Server to Server encryption is actually quite simple and requires nothing more than enabling SSL or TLS on the SMTP server and obtaining a $20 publicly trusted digital certificate on each server (tutorial on obtaining Digital Certificates). Unfortunately, not all companies and organizations have enabled Server to Server SSL or TLS communications but the technology is already there and the price of obtaining Digital Certificates has dropped to almost nothing.
The bottom line is that there is a lesson here for any individual or mail administrator who wants secure email. The technology is already baked, it often costs little or nothing to set it up and you just have to be willing to turn it on.