Everyone's least favourite ransomware is back and testing new infection tactics

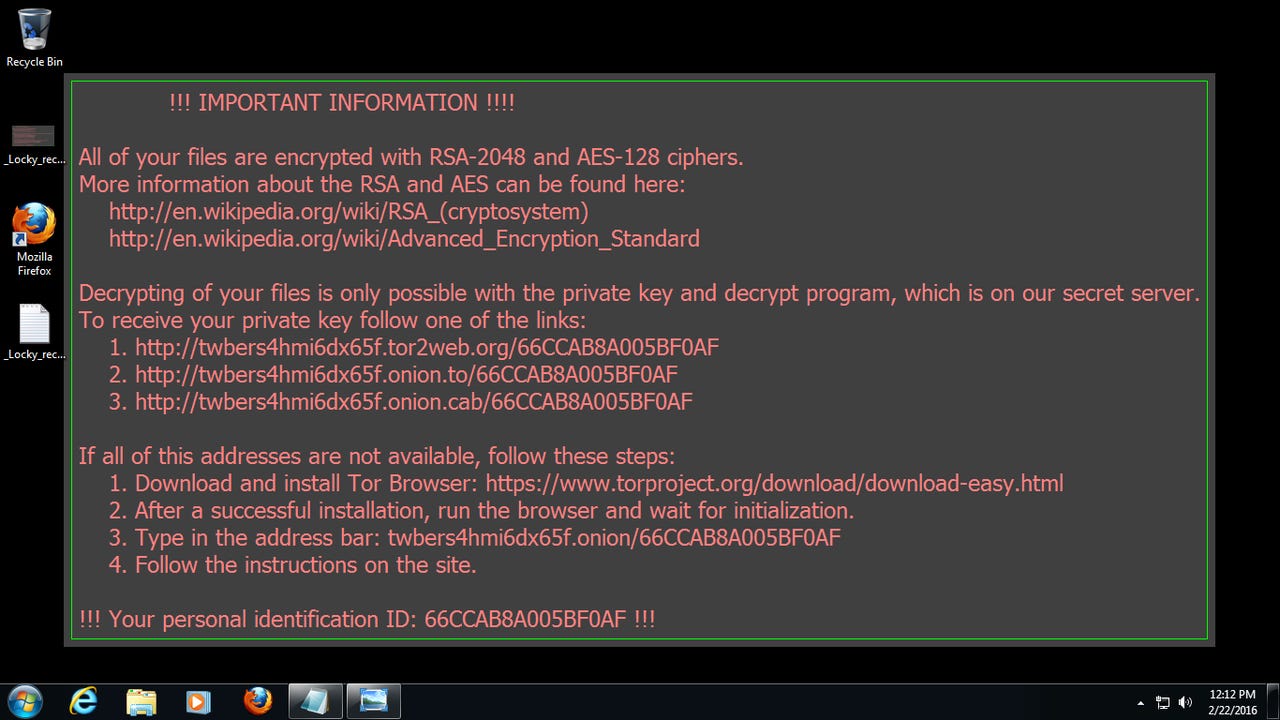
Locky was the most successful ransomware of 2016.
It was never going to fizzle out; one of the most prolific forms of ransomware is back after what appears to have been a holiday break.
Locky evolved to become the most notorious ransomware threat during 2016, even becoming the second most common malware threat by November. Locky ransomware campaigns dipped massively over Christmas, but cybersecurity researchers at Cisco Talos have noticed how attempts to deliver this form of ransomware are slowly beginning to rise again.
The main driver behind Locky campaigns is the Necurs botnet, which prior to the holidays was sending out hundreds of thousands of malicious spam emails containing the ransomware every day.
Researchers note that the revived Locky campaign is delivering fewer than a thousand messages a day - but it does appear to be leveraging some new tactics, which might be a test run before launching a new, full-on Locky campaign with new twists.
The first of the two new campaigns has been dubbed 'Double Zipped Locky' and sees cybercriminal perpetrators attempting to hide their malicious payload in a Zip file within a Zip file in the hope that the victim will think they're opening a document, instead of a malicious payload.
Currently, the Double Zip campaign is sent using the extremely basic format of a blank email containing the malicious attachment.
A sample of Double Zipped Locky
Not only does this particular new campaign infect victims with Locky ransomware, but the payload also delivers the Kovter Trojan. Even if the victim chooses to pay a ransom to criminals in order to unlock their files, Kovter remains on the infected system and is used to run click-fraud and malvertising campaigns.
A second new Locky campaign uses slightly sophistication than the blank Double Zip campaign in an effort to dupe victims, sending them an email posing as a failed transaction, telling the target their bank account has blocked some activity. Telling the target their account has seen suspicious activity is a common tactic for ransomware delivery.
Locky payload claiming to be information on a failed transaction.
But rather than delivering the malicious payload as a Zip file, this time it's hidden within a rar file, within which there's a malicious Javascript file which is used to retrieve Locky and install it on the infected machine, although in this instance, it uses methods much more commonly associated with delivering the Dridex banking trojan.
While both campaigns are currently operating at low volume, they could represent indicators that the sophisticated Locky machine is gearing up to continue its activities for 2017. It isn't the first time Locky has appeared to fade, as campaigns appeared to drop last summer before becoming more prolific once again.
Locky might have been slow to return, but other ransomware campaigns didn't take time off.
READ MORE ON CYBERCRIME
- Europol, Intel and Kaspersky team up to crack down on ransomware [CNET]
- Easy to carry out, difficult to fight against: Why ransomware is booming
- Progress in ransomware battle remains murky despite industry efforts [TechRepublic]
- How Bitcoin helped fuel an explosion in ransomware attacks
- The hackers that never went away: Brace for more state-backed attacks, leaks and copycats this year