Facebook 'likejacking' spam scams continue

Co-Authored with Tom Eston, SocialMediaSecurity.com
When Facebook first announced its external site "like" feature back in April, many security types pondered how it would soon be exploited for evil. The "like" feature is designed by Facebook so web developers can place the code anywhere they want on the web. Not only is it easy to use, but it is easy to abuse. While the feature has a lot of merit from a brand perspective, and it does help Facebook expand its social graph, anyone with a web site can use it. This has bred an entire new movement of Facebook spam scams -- called "likejacking" by many -- and has put the social network right back into a spot where it's comfortable: being reactive to security threats.
The latest scam has appeared as a potentially funny web site. The site in question, which tempts Facebook users with a note in a friend's news feed, claims to show the "15 worst construction mistakes EVER!" Users are greeted with a picture of two urinals placed precariously close to one another, and the instructions direct readers to click on the picture for more. Not only does clicking on the picture lead users to a journey down pop-up boulevard, but it automatically places a "like" note in that users own Facebook feed, with the intention of enticing that user's friends to do the same.
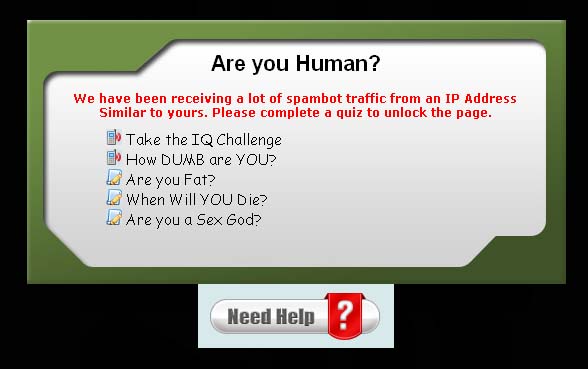
The first clue that there is something awry with the site is its URL, which indicates it provides "free Facebook layouts." Then, the page traps visitors with some fancy Javascript so that they cannot scroll down or leave the page without "taking a quiz." Even further, the page tries to scare visitors with a pop-up that says "We have been receiving a lot of spambot traffic from an IP Address Similar to yours. Please complete a quiz to unlock the page". This is a typical social engineering scare tactic popular with text messaging scams.
Clicking one of the links in the iframe sends a request to two additional affiliate programs, most likely collecting clicks for a CPA (cost-per-action) program. These requests happen so fast a user would have no idea other sites were being contacted. The main quiz page with the construction pictures are connected to a company called CPALeads.
After landing on the CPALeads page, there's an explosion of all different types of issues. Clicking on anything from this point on takes users to two different scam quiz sites, where they are presented with more questions that end up with a screen to enter their cell phone number. This text message scam has a sneaky terms of service that says that by entering a cell phone number, the user agrees to a $9.99 per month auto-renewing subscription service. The next page claims to show geolocation advertising showing other "quiz users" near you. And, if you try to get away from the page, the scam starts to get mean. It tells you that your friends think you are stupid. Free iPads are promised, which leads to additional text message scam recruitment, and page closing results in more pop-ups.
One interesting, and somewhat new scam characteristic, is that if a visitor is using an ad blocker like the Firefox extension Adblock Plus or NoScript while on that site there is a code to detect these tools and the page prompts users to disable these add-ons or to enable JavaScript. It will actually tell visitors how to disable the plugin with detailed instructions and screen shots.
The ever-present challenge of security is that scammers continue to get smarter, while general user education and safety enablement efforts are not keeping pace. With Facebook, it continues to create breeding grounds for these type to scammers by putting feature richness over user safety, and appearing to take the same reactive approach to its external "like" function that got it into so much trouble with its applications.
Note: While it appears that, as of publishing, Facebook has disabled this page from feeding spam into users' news feeds, it did proliferate for at least three days before it was disabled.