Fortune 500 companies use of email spoofing countermeasures declining
Here's a paradox - a technology originally meant to verify the sender of an email message for the sake of preventing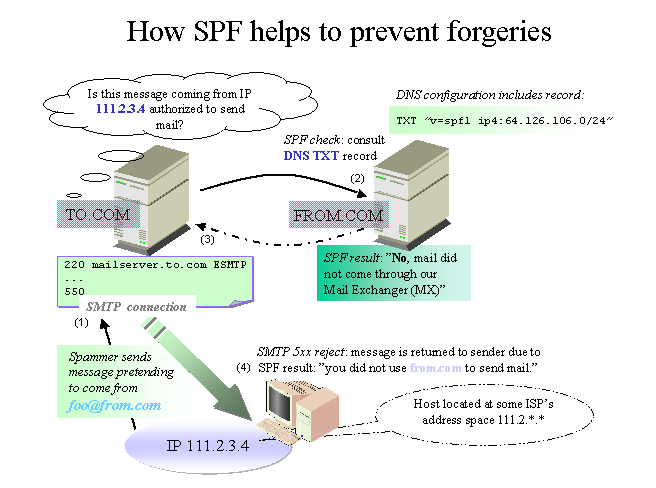
A recently conducted study by Secure Computing's TrustedSource reveals that, not only a mere 40% of the Fortune 500 companies use Sender Policy Framework and DomainKeys Identified mail, but also, that the ones who've implemented the countermeasures aren't fully taking advantage of protection mechanisms offered at the first place.
"Out of the 2008 roster of Fortune 500 companies, a mere 202 appear to be using any of the forgery countermeasures provided by SPF, DKIM, or similar implementations. This poses a stark contrast to Sendmail’s Survey, claiming some 90% of Fortune 1000 companies, suggesting a sharp decline from Sendmail’s reported 282 companies. To make sure our results were accurate, we decided against using a random sampling and instead put together a list of all 500 primary domains used by the Fortune 500 and query them.
A mere 202 companies, when you account for the companies running both technologies - 40% of the Fortune 500. To make matters worse, only 65 of the 167 companies using SPF included the -all policy, which causes a fail result to be sent if the IP address is not found explicitly in the policy."
And while the majority of Fortune 500 companies need to perhaps strategize better on how to built more authenticity in their communications and in fact prevent malicious attacks from reaching their mailboxes, spammers have been reportedly publishing SPF records since 2004, with MX Logic conducting a study into the tactic back then indicating that :
"In its preliminary study, MX Logic found that some spammers have embraced SPF in the hope that their unsolicited email messages will be viewed as more legitimate because the messages have an SPF email authentication record associated with them. In a sample of more than 400,000 unique spam email messages that passed through the MX Logic Threat Center from Aug. 29 through Sept. 3, 16 percent had published SPF records."
Things are a bit different today, with spammers as active participants in the cybercrime ecosystem constantly demanding
Here's an example of spammers sending DomainKeys Identified Mail from Yahoo's SMTP servers in April, 2008, found in a report issued by MessageLabs, a practice made possible due to the successful breaking of these services CAPTCHA based authentication, either automatically or through human based CAPTCHA breakers :
"The spam mails are sent via SMTP using Yahoo!’s servers, ensuring the message is signed correctly using Yahoo! DomainKeys Identified Mail (DKIM). This is a sender authentication technique that uses a digital signature in the headers to indicate that the message is genuinely from Yahoo! and not spoofed as such. This approach further helps to ensure that mail generated in this way is harder to block using anti-spam methods based on the source IP address; as if it had been sent from genuine Yahoo! mail servers. In most cases the spam messages are routed through the premium Yahoo! “Plus” servers which are not listed in the Yahoo! webmail interface options page.
The Yahoo! accounts appear to have been generated programmatically, presumably defeating the Yahoo! CAPTCHA mechanism, because of the consistent format in all cases and all have from-domain of @yahoo.co.uk currently. At the time of writing around 1,127 unique Yahoo! User IDs were used in the distribution of this latest type of spam over 28 days, with around 40 new IDs per day being generated."
As always, it's never been about the lack of technological solutions to eradicate all the junk and malicious emails hitting an organization's mailboxes and its customers. It's always been about the lack of implementation of these solutions, and ensuring that abusing the now trusted services isn't done as efficiently as it is for the time being.