Google Chrome extension that steals card numbers still available on Web Store

A malicious Google Chrome extension that can recognize and steal payment card details entered in web forms is still available on the Chrome Web Store.
The extension is the work of a cyber-criminal group and has been at the heart of a malware distribution effort in the past.
The website through which the extension was initially distributed is now down, but the extension is still available on the Play Store, meaning it could be used for future campaigns to infect new users.
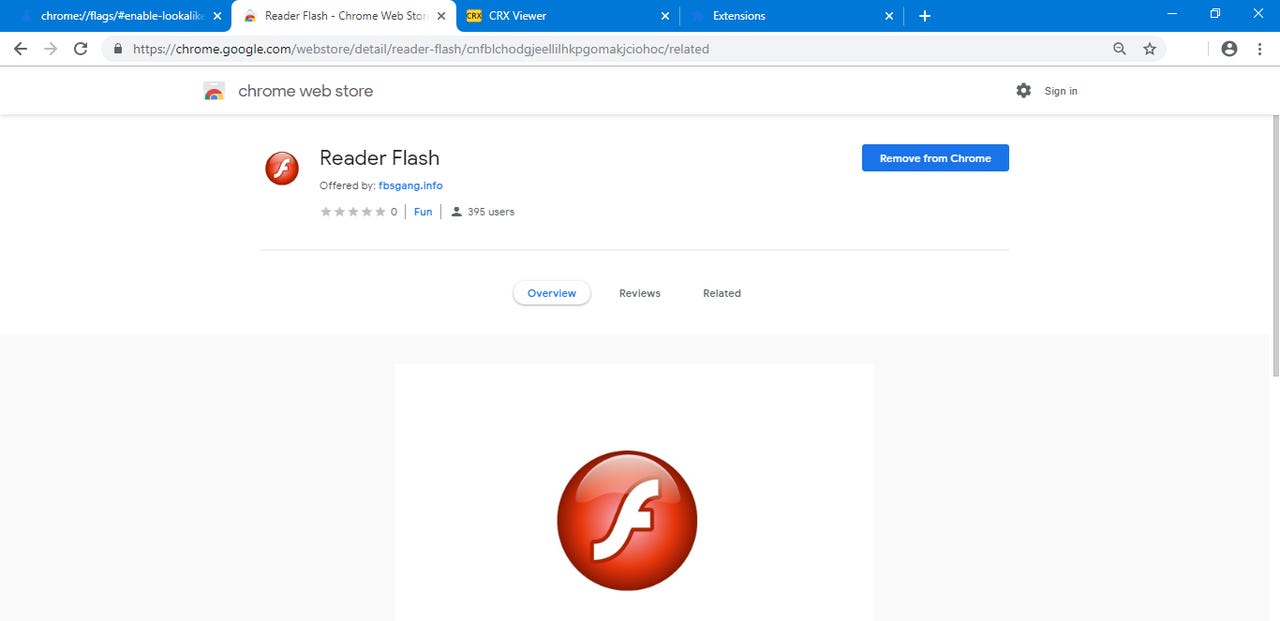
Until now, the extension has been installed by roughly 400 users, according to stats available on its official Chrome Web Store listing.
The extension's name is Flash Reader. According to a report from ElevenPaths, Telefonica's cyber-security division, the extension was distributed via http://fbsgang[.]info/flashplayer/, a page to which crooks redirected web traffic, possibly from malvertising campaigns or exploit kits.
The page used the classic lure of "you don't have Flash installed, use this Chrome extension instead," and redirected users to Flash Reader's official Chrome Web Store page to install it.
According to a review of the extension's code performed by this reporter and a third-party --to confirm ElevenPath's findings-- the extension contained code that intercepted any form submission made on any web page.
Regex rules would analyze the form's content for card number patterns specific to Visa, Mastercard, American Express, and Discovery card formats.
Once the extension would find the data it wanted, it would send the all the data entered in the current form to its command and control (C&C) server, located at http://fbsgang[.]info/cc/gate.php. This means it also collected card issuer names, expiration dates, and CVV/CVC codes.
This command and control server is now down, but C&C servers are often taken down between campaigns. This doesn't mean that users who have currently installed this extension are safe. Their card data was most likely already collected months before.
There is also the danger that the group could return with a new campaign, or push an extension update with a new C&C server address.
ElevenPaths researchers said they notified Google of the extension, which was uploaded on the Chrome Web Store in February last year. ZDNet has also sent an email to the Web Store team earlier today about the extension still being active.
One of the security researchers to whom ZDNet reached out suggested that the extension might have also been a test run for an upcoming campaign, although a test run that managed to infect 400 Chrome users, which, if anything, proves how easy is to get people to install crappy extensions without sparing a thought to security considerations.
UPDATE: An earlier version of this story claimed the extension didn't grab card names, expiration dates, and CVV codes. Further analysis by ElevenPaths and shared with this reporter revealed the initial conclusion was not true. The extension collects those details as well.
Top Google Chrome extensions (2019 edition)
More security coverage:
- Real-time location data for over 11,000 Indian buses left exposed online
- Hackers breach and steal data from South Korea's Defense Ministry
- Fortnite security issue would have granted hackers access to accounts
- Marriott says less than 383 million guests impacted by breach, not 500 million
- Advertising network compromised to deliver credit card stealing code
- WordPress to show warnings on servers running outdated PHP versions
- Firefox warns if the website you're visiting suffered a data breach CNET
- Marriott reveals data breach affecting 500 million hotel guests TechRepublic