Google: no evidence of a Gmail vulnerability
"With help from affected users, we determined that the cause was a phishing scheme, a common method used by malicious actors to trick people into sharing their sensitive information. Attackers sent customized e-mails encouraging web domain owners to visit fraudulent websites such as "google-hosts.com" that they set up purely to harvest usernames and passwords. These fake sites had no affiliation with Google, and the ones we've seen are now offline. Once attackers gained the user credentials, they were free to modify the affected accounts as they desired. In this case, the attacker set up mail filters specifically designed to forward messages from web domain providers."
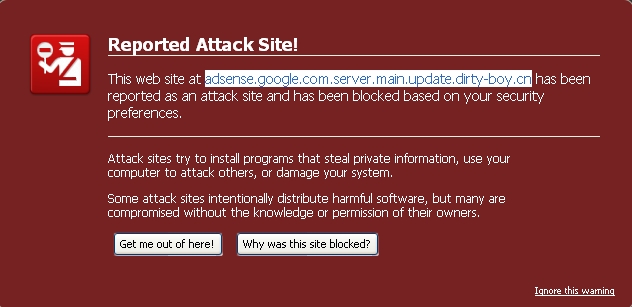
Phishing campaigns impersonating Google are in fact becoming so prevalent, that an entire market segment within the underground economy is starting to emerge, which is primarily trading with stolen AdSense accounts. Access to these accounts is obtained either through data mining already infected with malware hosts part of their botnet, or through plain simple phishing campaigns taking advantage of typosquatting in order to visually social engineer an end user, consider the following examples :
adwords.google.com.index.main.update .qwertycn.cn adsense.google.com.server.main.update .dirty-boy.cn edit.google.com.main.update .the-format.cn google.com.urchin.js .7traff.cn google.com.urchin.js .axa1.cn adwords.google-secutiyserv .com google.com.br.updatesoftware.index.d81f0f02cd6a877358cde8fbdbad89a5 .qwertycn.cn google.com.updatesoftware.index.d81f0f02cd6a877358cde8fbdbad89a5 .rootit2.info adwords.google.com.session-69680268279998252722.92444537268559875865 .com68.ru
Two weeks ago, Google quietly fixed a critical XSS vulnerability affecting its accounts login page, which at the time was providing a fully realistic opportunity for malicious attackers to turn into "cookie monsters" and hijack user's sessions on a large scale.