Hackers going corporate with new attack attitudes, research shows

It's a mean and nasty cyber world out there, and it's getting more organized.
Symantec's latest Internet Security Threat Report, which looks at 2015, concludes that cybercriminals are going corporate - not for raids - but in establishing best practices and conducting their affairs like a business.
The spinoff of those efforts was equally troubling. In 2015, Zero-Day attacks doubled to 54 (the most ever). And malware revealed 430 million new variants.
The measurable results were down right scary, including the largest data breach ever with 191 million records compromised from an improperly configured database of registered U.S. voters. In 2015, there were a record nine mega-breaches (minimum 10 million records), 429 million identities stolen, a 35 percent growth in crypto-ransomeware attacks, and a resurgence of familiar deceptions including a 200 percent rise in fake tech support scams.
But it wasn't just the action of hackers that researchers noted. It also was the fact that breached companies aren't always reporting accurately.
"The increasing number of companies choosing to hold back critical details after a breach is a disturbing trend," Kevin Haley, director of Symantec Security Response, said in a release accompanying the report's findings. "Transparency is critical to security. By hiding the full impact of an attack, it becomes more difficult to assess the risk and improve your security posture to prevent future attacks."
The researchers put end-users on notice to kick bad habits, such as sharing passwords. Research showed that more than a third of users who share passwords had shared their banking password.
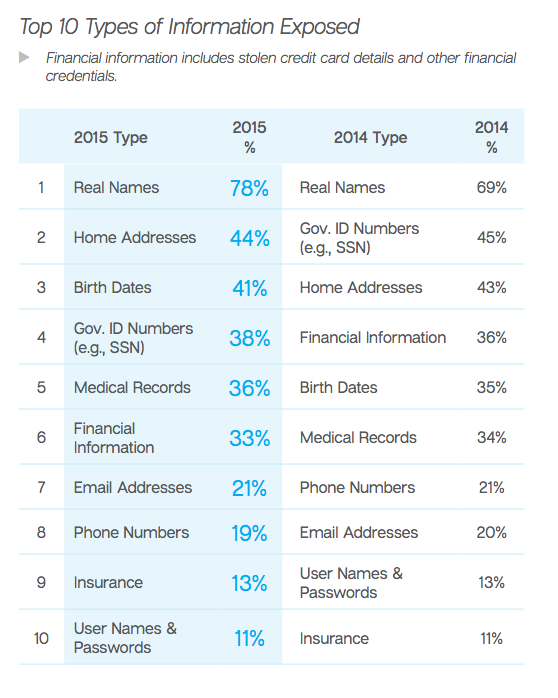
Passwords, however, dropped to the bottom of the Top 10 list of most exposed data. The numbers went from 13 percent to 11 percent in 2015 when compared with 2014 (when passwords were No. 9). The researchers repeated advice on password policies, calling for passwords of at least 8-10 characters that include a mixture of letters and numbers, for users to stop re-using passwords and to for a password change every 90 days.
The researchers called on cloud services to take care with data and control access, preferably with two-factor authentication. The report, however, noted concerns with some 2015 attacks that used sophisticated social engineering to bypass two-factor authentication that used SMS messaging to transmit codes via mobile devices.
The most common data collected in breaches were real names, which were pilfered in 78 percent of data breaches. Forty to 30 percent of breaches collected home addresses, birth dates, Government IDs, medical records, and financial information, while 10 to 20 percent claimed email addresses, phone numbers, insurance information, and user names/passwords.
The researchers noted an increase in proof-of-concept attacks in the Internet of Things (IoT) category and a growing numbers of IoT attacks in the wild. The issues were typically with careless implementations around authentication and encryption (or the lack thereof), including remote take-over of cars, hacks on keyless entry systems, smart home devices, medical devices, smart TVs, and embedded devices.
Symantec researchers offered these best practices for businesses:
- Educate users on safe social media conduct.
- Encourage users to adopt two-step authentication on any website or app that offers it.
- Ensure users have different passwords for every email account, applications and login―especially for work-related sites and services.
- Remind users to use common sense.
- Encourage employees to raise the alarm if they see anything suspicious.