ICSA Labs: Security products often fail and are insecure

Almost 80 percent of security products fail when first tested and require two rounds of testing before being certified, according to a report from ICSA Labs.
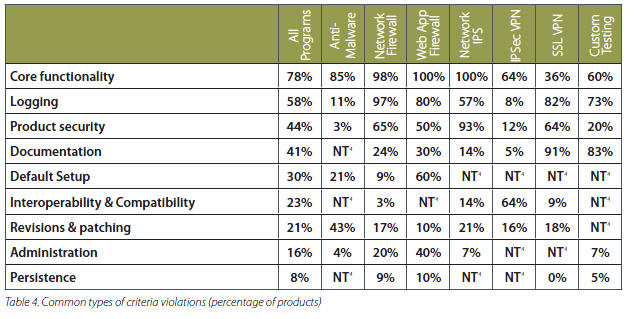
ICSA, a unit of Verizon Business, looked at 20 years of data about security products to cook up that figure. ICSA tests security products and certifies them. So why do these products flop out of the gate? Simply put, security software doesn't perform as it should. Core functionality---for instance an anti-virus product failing to prevent infections---accounted for 78 percent of failures. In fact, only 4 percent of products pass the first round of ICSA testing.
Logging was the second biggest reason for initial failures. Incomplete or inaccurate logging of who did what and when accounted for 58 percent of failures. Ninety-seven percent of network firewalls and 80 percent of Web application firewalls have at least one logging problem.
George Japak, managing director of ICSA Labs, said that logging has been a pain for vendors because it just isn't a focus. However, enterprises need logging for regulatory requirements. "Logging in recent years has had higher prominence in recent years," said Japak.
The other notable finding is that 44 percent of security products had their own security issues. Japak noted that ICSA has seen a bevy of firewall products with cross-site scripting products. Simply put, security software is riddled with faulty programming.
Wade Baker, research and intelligence principal with Verizon Business, said developers haven't focused on security until recently. "It's relatively recent that developers are starting to think like attackers," said Baker.
The ICSA report has a bevy of interesting items. Here's the money quote:
Are the security products your organization depends upon every day reliable? Do they consistently meet expectations and live up to their billing? Chances are they do not. This experience has resulted in the not-so-tongue-and-cheek postulation that new security products are created to compensate for the shortcomings and side effects of the existing ones. That’s not to say there is never a legitimate need for new security solutions; new business models, new technologies, new threats, and new levels of global interconnectedness require us to continually adapt the products and practices we employ to protect information assets.
Unfortunately, the market’s solutions to all this newness are not always as legitimate as the need. Product quality is often left behind in the rush to be latest and greatest. New is distorted with innovative bigger touted as better, and promises frequently exceed performance. Thus, the work of helping to distinguish fact from fiction is critical.
And here's a look at ICSA's aggregate scorecard: