Jira bug exposed private server keys at major companies, researcher finds

(Image: ZDNet)
Several tech giants and major companies are exposing private server keys, thanks to a bug in widely used development software, which could allow a hacker to gain a foothold into their corporate networks.
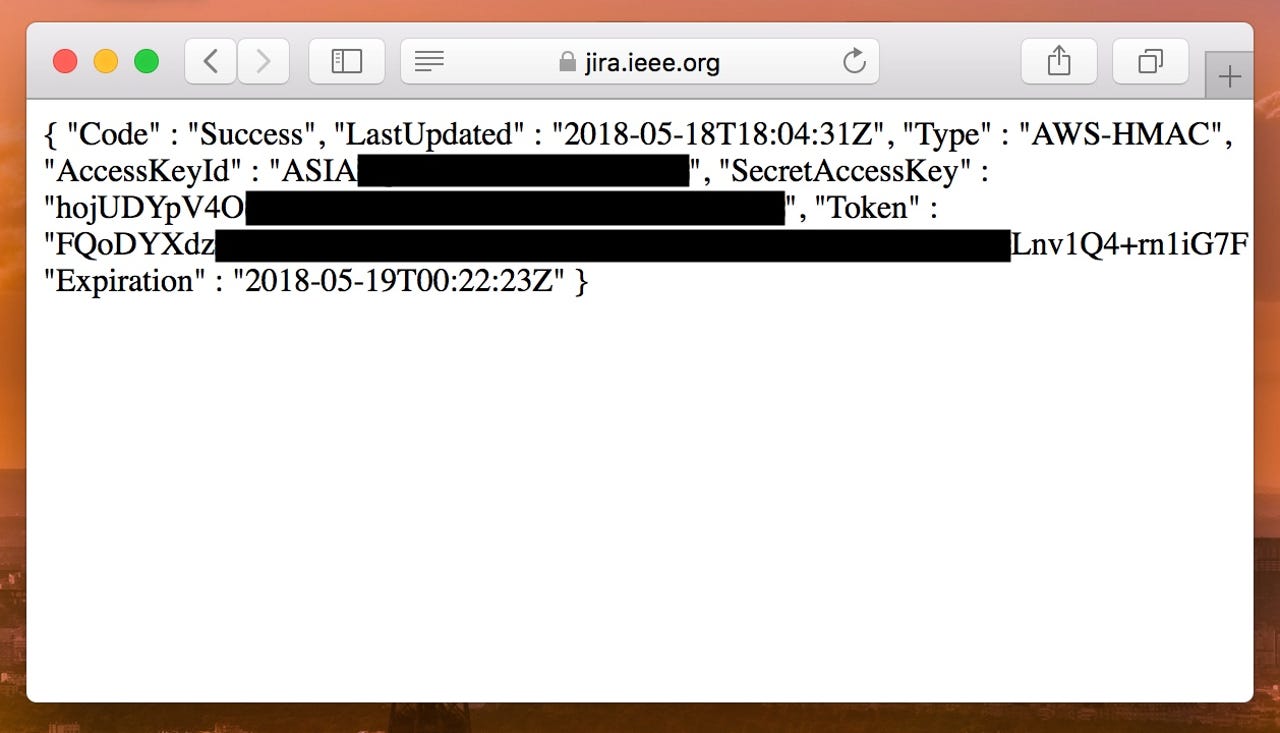
The bug, found in Atlassian software like Jira and Confluence, lets anyone easily obtain the secret access keys to the Amazon Web Services (AWS) instance that the software is hosted on.
It's because older versions of the software contains a vulnerable proxy, which can be abused to carry out cross-site scripting (XSS) attacks, and server-side request forgery (SSRF) attacks that return sensitive data from within the internal network.
Featured
An attacker can use an SSRF attack against the vulnerable proxy to siphon off AWS metadata such as secret access codes, as documented last year in a bug report.
Those keys in the hands of an attacker could result in a takeover of the instance, leading to data theft or destruction.
NIST gave the bug a 6.1 out of 10 severity rating on Atlassian products, all of which were fixed in March 2017.
Although most deployments have been updated, many companies are still running legacy versions of the software, often hosted on a company's subdomain or are easily searchable. Security researcher Robert Wiggins found over a dozen major companies running out-of-date and exposed Jira and Confluence deployments.
Several companies -- and one US government agency -- have updated their deployments after we reached out.
A spokesperson for EE, the largest cell network in the UK -- which recently left a critical code system online -- confirmed the company had fixed its vulnerable Jira deployment.
Insider, a growth management platform, also fixed its Jira deployment after we reached out.
Easy Metrics, a cloud-based productivity software house, was running a vulnerable version of Jira. A spokesperson said the company "opted to shut down the instance and migrate our Jira workflow into the cloud," and will notify any clients that may be affected.
A division of the US Dept. of Health and Human Services, the Agency for Healthcare Research and Quality, pulled its vulnerable Jira server offline.
IEEE, a professional body for engineers, fixed its internal Jira deployment after we reached out.
"Once we became aware of this matter, our team worked diligently to follow our security procedures," a spokesperson said. "We have confirmed that the issue is resolved and no personal data had been exposed."
Ronin, a cloud-based research software maker, secured its vulnerable Jira server, which the company's chief executive Nathan Albrighton said was "isolated to our development environment," but declined to comment further.
And, A&E Networks, a television and media giant, also left a vulnerable server exposed. The server was shut down, and the company declined to comment on the record.
At least three companies -- a musical instrument maker, a footwear retail giant, and a sports governing body -- did not return several emails warning of the bugs, and remain vulnerable.
For that reason, we're not naming the affected companies.
It's thought that there are many other vulnerable deployments. Earlier this year, two Jira instances run by the US Dept. of Defense were fixed, according to one bug bounty write-up.
If you haven't already -- and you've had over a year -- updating your Atlassian software sounds like the best solution.