Mac OS X malware posing as fake video codec discovered
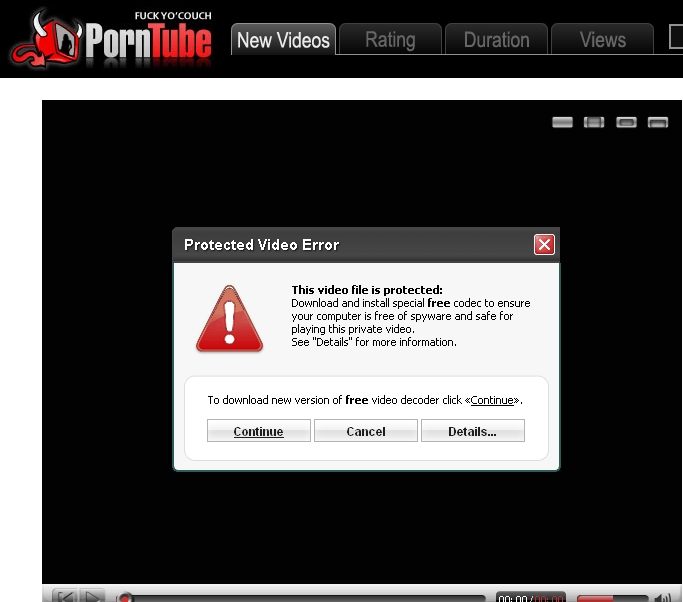
The use of fake video codecs is a social engineering tactic exclusively used by malware targeting Windows, and seeing it used in a Mac OS X based malware attack proves that successful social engineering approaches remain OS independent.
Prior to PareteLogic's sample, SophosLabs appear to have received an email from the author of last month's discovered OSX/Tored-A sample, allowing them to add generic detection for any upcoming releases.
Here are some of the PornTube templates used in the social engineering attack, a description of the malware, as well the descriptive filenames used in some of the campaigns:
OSX/Jahlav-C is described as:
"OSX/Jahlav-C is a Trojan created for the Mac OS X operating system. The initial malicious installer is distributed as a missing Video ActiveX Object.
As a part of the installation a malicious shell script file AdobeFlash is created in /Library/Internet Plug-Ins folder and setup to periodically run. The script contains another shell script in an encoded format which in turn contains a Perl script with the main malicious payload. The perl script uses http to communicate with a remote website and download code supplied by the attacker."
What's Apple's take on this emerging trend?
Earlier this week, in a rare comment of potential Mac OS X related insecurities in the face of malware, the company not only acknowledged OS X Malware, but also pointed out that :
"The Mac is designed with built-in technologies that provide protection against malicious software and security threats right out of the box. However, since no system can be 100 percent immune from every threat, antivirus software may offer additional protection."
Is the company finally taking the right decision to generate security awareness on a threat that is prone to become a daily routine in the long term, or was it too slow to stop using the Mac's massively advertised immunization to malware as a key differentiation factor?
What do you think?
Talkback.