Malicious Chrome extension caught stealing Ledger wallet recovery seeds

A malicious Chrome extension is targeting owners of Ledger cryptocurrency wallets, Harry Denley, Director of Security at the MyCrypto platform, discovered today.
Ledger wallets are small hardware devices that can be used to store the private keys (passwords) needed to access cryptocurrency accounts. These wallets support multiple cryptocurrency formats and provide a way for users to store the private keys for all their cryptocurrency in one place, in an offline format, safe from web-based attacks and phishing attempts.
In theory, using a Ledger wallet should mean users are not at any risk, but it turned out not to be the case.
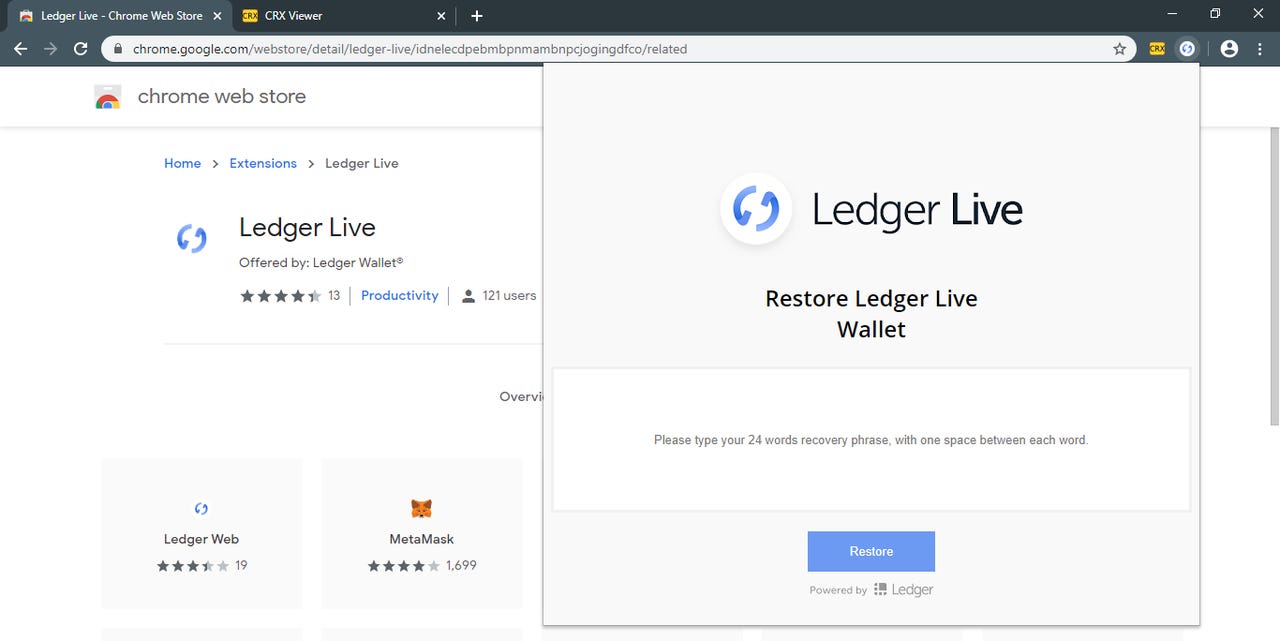
Today, Denley discovered a Chrome extension named Ledger Live that tries to pass as the real Ledger Live, a mobile and desktop app that allows Ledger wallet users to query their funds and approve transactions by syncing their hardware wallet with a trusted device.
The malicious extension tries to trick users into thinking this is the Chrome version of the original Ledger Live app, which would allow them to do the same thing (check balances, approve transactions) through the Chrome browser.
Users are told to install the extension and connect (sync) their Ledger wallet to it by entering the wallet's "seed phrase."
This seed phrase is a string of 24 words that is used to move wallet data between devices -- as a wallet recovery system in case users lose or want to change devices.
But Denley says the extension is a fraud and does nothing except to show a popup that, in reality, collects and sends the user's Ledger seed phrase to a Google Form.
In an interview, Denley told ZDNet that the person behind this malicious extension can use the stolen seed phrases with their own Ledger wallet and "recover" other users' Ledger wallets -- most likely to gain access to their accounts and steal funds.
"When you set up a Ledger wallet device, you are given the mnemonic [seed] phrase for recovery. They [Ledger] have good instructions on keeping this private information offline, not shared, and in a secure place," Denley told ZDNet.
"The extension makes no sense to install and use because it defeats the purpose of having a hardware wallet with your secrets offline," he added.
"But I would not be surprised if it has got people to input their secrets," Denley said. "It's a big problem in the cryptocurrency area, to teach people their private keys/mnemonics should stay offline."
Promoted through Google ads
Currently, the extension is still available through the official Chrome Web Store, where it lists more than 120 installs.
Since Ledger hardware wallets are used to manage more than 20 types of cryptocurrency accounts, a hacker who manages to steal a Ledger seed phrase could gain access to large amounts of cryptocurrency.
Furthermore, according to Denley, the extension is also heavily advertised via Google ads for the keywords "Ledger Live," the Ledger service it's trying to impersonate.
This is being delivered by @GoogleAds under search phrase "Ledger Live"
— harrydenley.eth ◊ (@sniko_) March 4, 2020
cc: @Ledger @Ledger_Support pic.twitter.com/zrnxXqhHbb
Earlier this year, Denley caught another malicious Chrome extension, similarly engaged in stealing private keys to access cryptocurrency wallets and accounts.