McAfee fails the Conficker test

Update: 31-Mar, 4PM PDT: McAfee has corrected the errors on the web pages associated with its Stinger downloads. Joris Evers, McAfee's director of worldwide PR, writes via e-mail: " It's unfortunate that you don't like the way we present the Conficker information on our Web site, but there is a lot out there including a front page banner that leads to a landing page that went live early this week." He points to the company's main landing page for Conficker information, which contains a link to a Conficker-specific version of the Stinger tool, and to a 15-page PDF document entitled "Finding W32/Conficker.worm," He also notes that McAfee's Avert Labs has "blogged numeroius times about conficker."
The hysteria over the Conficker worm is reaching a fever pitch, with mainstream media doing their bit to whip Windows users into an unjustified panic over something that will affect a tiny fraction of the user community, made up almost entirely of people who were too stupid or negligent to apply a Windows patch issued nearly six months ago.
Ironically, many security professionals are in the amusing position of having to tamp down the hysteria. See, for example:
- Please, the world is NOT ending on April 1 (Sunbelt Software)
- Watch out for the Honda Accords (ESET)
- Conficker April Fools Hype (SecureWorks)
The trouble with virus scares is that they do a wonderful job of driving people directly into the arms of rogue security vendors (thank you, F-Secure). What makes this phenomenon even worse is when one of the largest security companies in the world creates a website filled with sloppy mistakes that make it look exactly like a rogue vendor.
Yes, I’m talking about you, McAfee. Let’s go through the list.
For starters, McAfee’s W32/Conficker.worm information page is hosted at a very strange URL: http://vil.nai.com/vil/content/v_153464.htm. Now, an old-timer like me will remember that McAfee Inc. used to be Network Associates, Inc. (NAI) until about five years ago. So I didn't find that nai.com domain too alarming. But a casual computer user certainly won't know that obscure bit of corporate history, and the McAfee logo and name are splashed all over that page, even though the domain name is completely unrelated. You know, like rogue security sites do.
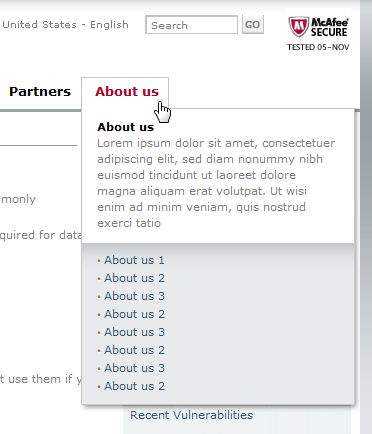
On its home page, under a bold red “BREAKING ADVISORY” head, McAfee has also helpfully noted that it has “posted a W32/Conficker-specific version of our Stinger tool.” Following that link takes you to the Avert Tools download page and then to a download page for the tool itself (many third-party sites link directly to this page). Like the Conficker info page, the Stinger download page is hosted at nai.com even though the McAfee name is the only one used on the page. One IT pro I spoke with was convinced this was a bogus download after he went to the Stinger page, clicked the About Us link, and saw … well, see for yourself:
Sloppy website design or a rogue site? If you’re a nervous Windows user who’s been told that the world’s most dangerous computer worm is going to strike tomorrow, do you trust this site? Me neither.
And as long as we’re picking on sloppy web designers, take another look at the McAfee Secure logo in the upper right corner of that page. According to the logo, this page was last tested by the McAfee Secure service on November 5 (2008, I presume, but who knows?). For the record, that’s nearly five months ago. McAfee’s home page carries a current date in this spot.
Security is serious business, and details matter. When a company as large as McAfee is this sloppy with its public response to a high-profile issue, it makes you wonder how tightly the engineering, development, and support sides of the business are being operated.
My advice: If you're looking for a reliable source of security information, skip McAfee.