Microsoft: Macs 'not safe from malware, attacks will increase'

Microsoft researchers have analyzed a new piece of Mac malware that uses a multi-stage attack similar to typical Windows malware infection routines. In a post titled "An interesting case of Mac OSX malware" the Microsoft Malware Protection Center closed with this statement:
In conclusion, we can see that Mac OSX is not safe from malware. Statistically speaking, as this operating system gains in consumer usage, attacks on the platform will increase. Exploiting Mac OSX is not much different from other operating systems. Even though Mac OSX has introduced many mitigation technologies to reduce risk, your protection against security vulnerabilities has a direct correlation with updating installed applications.
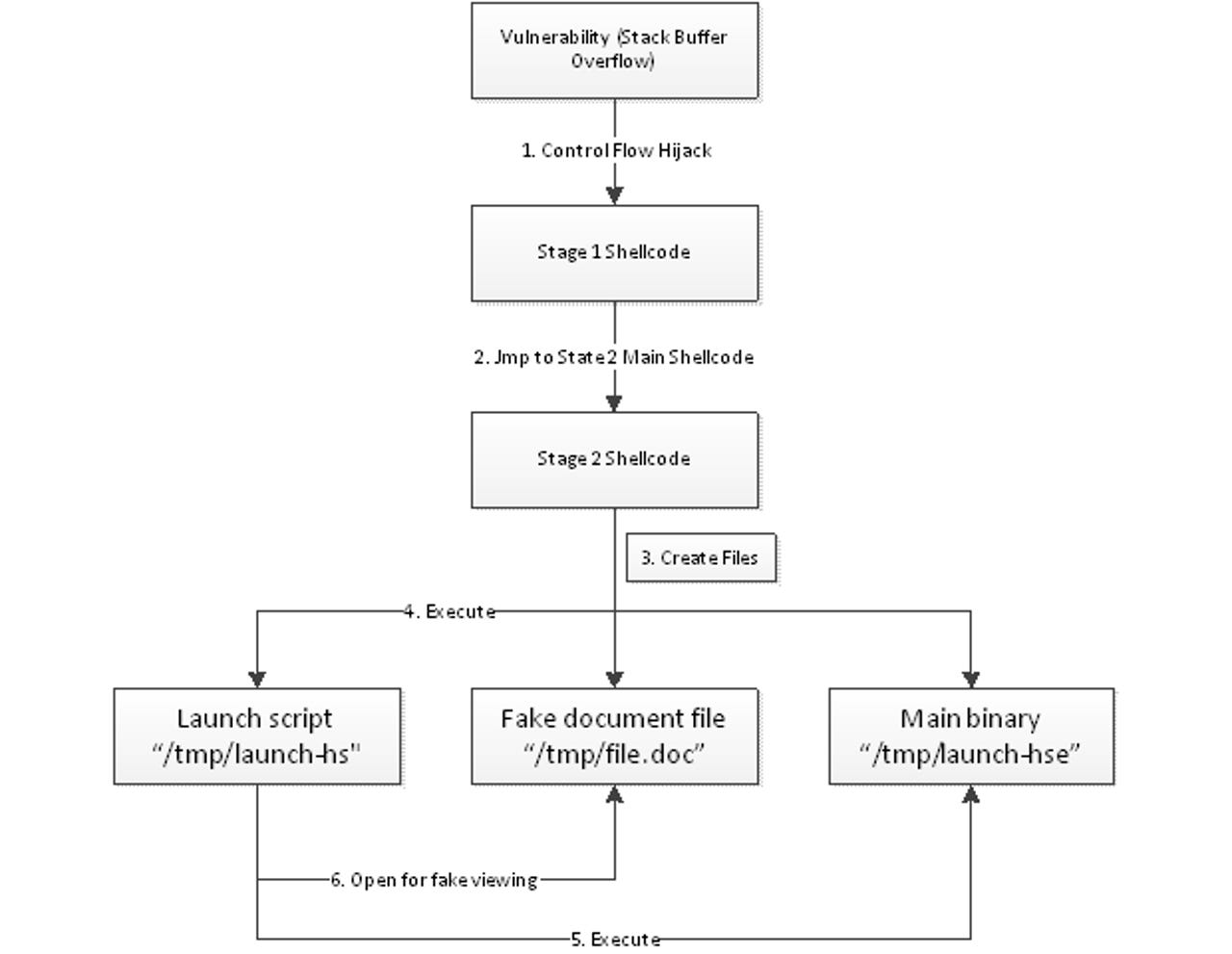
So, what was the piece of code that caused Microsoft to write this? The malware in question uses a stack-based buffer overflow as an entry point for executing two-stage shellcode on a Mac that eventually leads to the installation of a bot that connects to a remote command-and-control (C&C) server. Thankfully, the exploit in this specific piece of malware only works on Snow Leopard and older versions of Mac OS X because the particular address it uses to write to isn't writable in Lion.
Here's the software giant's description:
Firstly, the vulnerability is a stack-based buffer overflow - the attack code could corrupt variables and return addresses located on the stack. As we analyzed the malware, we found that the malware author managed to corrupt a local variable and used that corrupted variable to deploy 'stage 1' shellcode to a designated area. This corrupted variable is later used for a target address and is where the stage 1 shellcode is copied. The corrupted return address points to this target address as well.
This target address is important, as, with Snow Leopard, we could confirm that it was used to exploit a specific location on the heap that is writable and also executable. The point is, that with Lion, that specific memory address can't be written, so the exploit fails.
We can assume that this malware itself is targeting only Snow Leopard or lower versions of Mac OSX. That means the attacker had knowledge about the target environment beforehand. That includes the target operating system, application patch levels, etc.
This stage 1 shellcode leads to stage 2 shellcode, which is located in memory. The stage 2 shellcode is actually where the infection of the system occurs.
If you want to check for this particular malware, you'll want to know that it creates the following three files:
- /tmp/launch-hs
- /tmp/launch-hse
- /tmp/file.doc
Each of the files on the infected machine performs a separate function. The file called "launch-hse" is the end payload of the attack. It communicates with the C&C server controlled by the attacker, which can perform a number of actions on the infected machine, including deleting files, gathering information about the OS and hardware, as well as uninstalling itself from the Mac.
While this is all certainly interesting, I'm most concerned that this malware uses a three-year-old flaw in Microsoft Office 2004 for Mac, Microsoft Office 2008 for Mac, and Open XML File Format Converter for Mac. Here's the corresponding security bulletin: MS09-027 - Critical.
Why is this a big deal? For one, Microsoft patched this flaw 35 months ago. Secondly, this particular security hole was exploited by a different piece of Mac malware just a few weeks ago. That's worrying. Here's what I wrote at the time:
You'll need to update Microsoft Office 2004 for Mac and Microsoft Office 2008 for Mac. Thankfully, this security vulnerability is from June 2009, so if you keep your Microsoft software patched, you should be good to go.
The same advice applies. Unfortunately, it appears that many Mac users, just like many Windows users, don't keep their software up-to-date.
See also:
- Cross-platform malware exploits Java to attack PCs and Macs
- New Flashback variant silently infects Macs
- New version of Mac OS X Trojan exploits Word, not Java
- New targeted Mac OS X Trojan requires no user interaction
- Over 600,000 Macs infected with Flashback Trojan
- How big a security risk is Java? Can you really quit using it?