Microsoft proposes "invitation mechanism" for secure social networking behind enterprise firewalls

Ask any security-conscious enterprise sys admin (hopefully they are all born with the security gene) and they will tell you that they dread outside social networks.
In more cases than not, these social networks are firewalled.
Apparently sensing the need for a more secure path for contact with social networks through and behind the enterprise firewall, Microsoft has just published a new Patent application entitled Integration of Social Network Information and Network Firewalls.
This Patent application's Abstract gives us the basics:
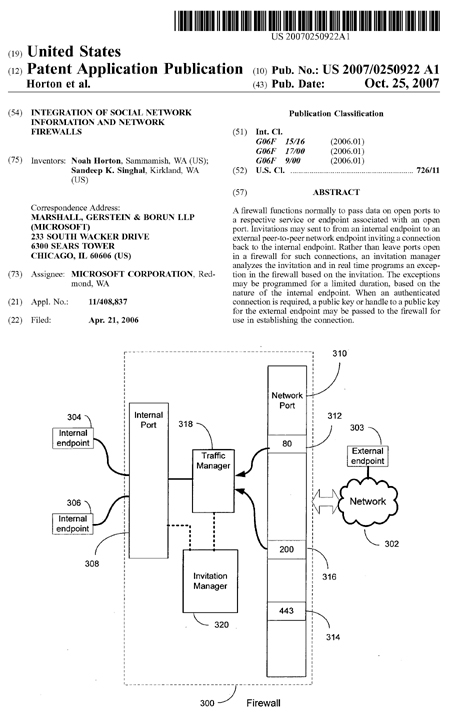
A firewall functions normally to pass data on open ports to a respective service or endpoint associated with an open port. Invitations may sent to from an internal endpoint to an external peer-to-peer network endpoint inviting a connection back to the internal endpoint.
Rather than leave ports open in a firewall for such connections, an invitation manager analyzes the invitation and in real time programs an exception in the firewall based on the invitation.
The exceptions may be programmed for a limited duration, based on the nature of the internal endpoint.
When an authenticated connection is required, a public key or handle to a public key for the external endpoint may be passed to the firewall for use in establishing the connection.
More detail is available in the literature for this app:
Instead of manually entering an allowed IP address or list of remote users to allow for setting a firewall exception, an invitation mechanism may be programmed to extract data about a connection invitation sent to an outside party and to appropriately program the firewall exception.
The exception may be specific to the particular connection invitation, and, optionally, for limited duration. The invitation mechanism may be associated with an application, for example, an instant messaging program, or a game.
Alternatively, the invitation mechanism may be part of an operating system callable by an application or trapped by the OS itself. The firewall may receive an application handle and an identifier for the outside party, such as cryptographic material.
The cryptographic material may be a public-key. The identifier for the outside party may be a handle, or pointer, to the public-key or an equivalent, such as a certificate. The exception may be timed corresponding to the type of application or invitation.
For example, an exception for an e-mail-based invitation may be available for a period of hours, whereas an IP-based invitation for a game may be available for a minute or less. By making available the cryptographic material (e.g. public key) for an IPsec connection, the firewall can process the connection without interruption to the application, user, or OS.
Aggressively and creatively applied/prostelitized, this technology could soften some enterprise institutional resistance toward communicating with outside social networks.