Microsoft to ship emergency IE, Visual Studio patches

Less than a month after a first pass at patching a troublesome flaw affecting its dominant Internet Explorer browser, Microsoft has announced plans to release two emergency updates with a comprehensive fix for the problem.
The unusual move comes on the heels of a bombshell blog post by reverse engineering specialist Halvar Flake that the original IE kill-bit fix was "insufficient" and that Microsoft "might have accidentally introduced security vulnerabilities into third-party products."
Microsoft declined to discuss specifics of the emergency patches until tomorrow (July 28, 2009) but a source tells me that it is directly linked to the Microsoft Video ActiveX Control (msvidctl.dll) issue that was being exploited in the wild.
[ SEE: IE users beware: Zero-day attacks hit Microsoft Video ActiveX Control ]
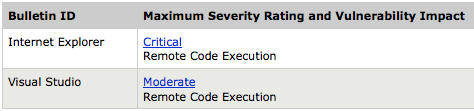
Tomorrow's out-of-band updates will address:
- One bulletin will be for the Microsoft Visual Studio product line; application developers should be aware of updates available affecting certain types of applications.
- The second bulletin contains defense-in-depth changes to Internet Explorer to address attack vectors related to the Visual Studio bulletin, as well as fixes for unrelated vulnerabilities that are rated Critical.
Interestingly, the issue of using kill-bits to secure IE from ActiveX control vulnerabilities will take center stage at the Black Hat security conference this year. IBM X-Force researcher Mark Dowd will show how these kill-bits can be bypassed [video demo] to launch code execution attacks.