New anatomy of a hack

As a white-hat hacker for a big audit firm I spent days and nights in our “lab” launching scans and scripted attacks against client networks. Other than the possession of a “get-out-of-jail-free card”, a signed agreement from the customer, our methodologies were the same as any hacker’s.
Eventually I developed the following slide to better describe the anatomy of a hack.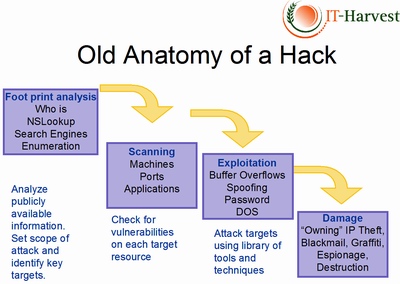
The most interesting stage of a targeted attack is the reconnaissance, or footprint analysis. Here you use the web, search engines, whois, and nslookup, to discover as much about the target as possible. A whois lookup can tell you email address formats for instance (first letter last name @ company.com). An improperly configured DNS server could reveal machine names to an nslookup query (payments.company.com). A Google search could reveal submission to forums by security personnel that reveal brands of firewall or antivirus in use at the target. Sometimes network diagrams are even found that can guide an attack. The next stage, scanning, meant using special tools, ( I date myself by mentioning Cybercop and Internet Security Scanner, these were the days before the open source Nessus) to discover open ports, services, and machines on the target network. And then, finally, you could start attacking various vulnerabilities that you had discovered.
This cook-book methodology is still the same used by attackers and security consultants that are hired to test your preparedness. However, as I looked at that slide in preparation for a seminar I am giving on the security market, I realized that it needs to be updated to account for recent developments: in particular, the use of Trojans to slip inside a network and steal information directly.
The new anatomy of a hack looks like this picture.
The attacker still needs to know their target, and thus the footprint analysis, but then they proceed to use custom viruses and Trojans to infiltrate the target. The Trojans then harvest files, email, and keystrokes and send them back to home base. What is chilling is that this is so much easier than the old methodology. And, according to the National High Tech Crime Unit in the UK(now SOCA), it is being used against UK businesses and government agencies on an industrial scale.