Optimising and securing your network

The first line of defence is the SSID, which can be up to 32 characters in length. Make sure you change this to a unique network name right away. Leaving the factory-default setting in place -- typically 'wireless', 'any' , or the manufacturer's name -- is like leaving your house's front door open. You guard your network's 'back door' by setting the WEP encryption on the AP and the clients. Although the AP can create and distribute a new WEP key for each session, the network still must broadcast the key through the air, which can compromise security. Manufacturers promise an update to the security protocol in the near future, but in the meantime we suggest you enter a key manually on both the AP and the client. Unfortunately, this means you must enter 26 letters and numbers for a 128-bit key. You should also choose a random sequence of letters and numbers, and then change it frequently.
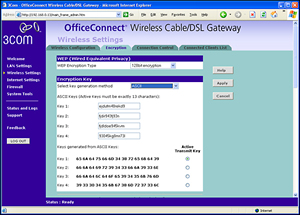
Wireless Settings configuration screen for the 3Com OfficeConnect Wireless Cable/DSL Gateway.
What, me worry?
Still worried about security? You could set the EAP on the access point to authenticate only those clients with a smart card or other high-level security device -- if you use one of the few notebooks that support them. Alternatively, you can use a proprietary security system to lock the network's windows as well as its doors. One of our favourites is Kerberos, which was developed at MIT and named for Greek mythology's three-headed guard dog at the gates of Hades. It works with all major operating systems except Mac; it sends out keys in encrypted form, so snoopers would have to work hard to break in.
You can also keep evildoers out by turning off DHCP. Instead, give an exact IP address or range of IP addresses for your computers. Theoretically, the hacker will be stuck on the outside of your network. You can also set the AP to allow only a predetermined list of MAC addresses to connect or to have full network access.
With so many different parameters to keep track of, we suggest you write them all down. If you're at home, put the AP's IP address, SSID, WEP level and other details on a card, then tape it on the back of the AP or keep it with the documentation. Office users should keep all the network settings in a secure location.