Popular security suites open to attack

Tests by independent test lab AV-Test.org show that few of them consistently use important techniques to protect their executables against vulnerability exploit.
The main techniques are DEP (Data Execution Prevention) and ASLR (Address Space Layout Randomization). DEP protects against many buffer overflow exploits, usually by using CPU features to mark certain areas of memory as not executable. ASLR protects against attempts to execute privileged code at known locations in memory by randomly locating executable code at load time.
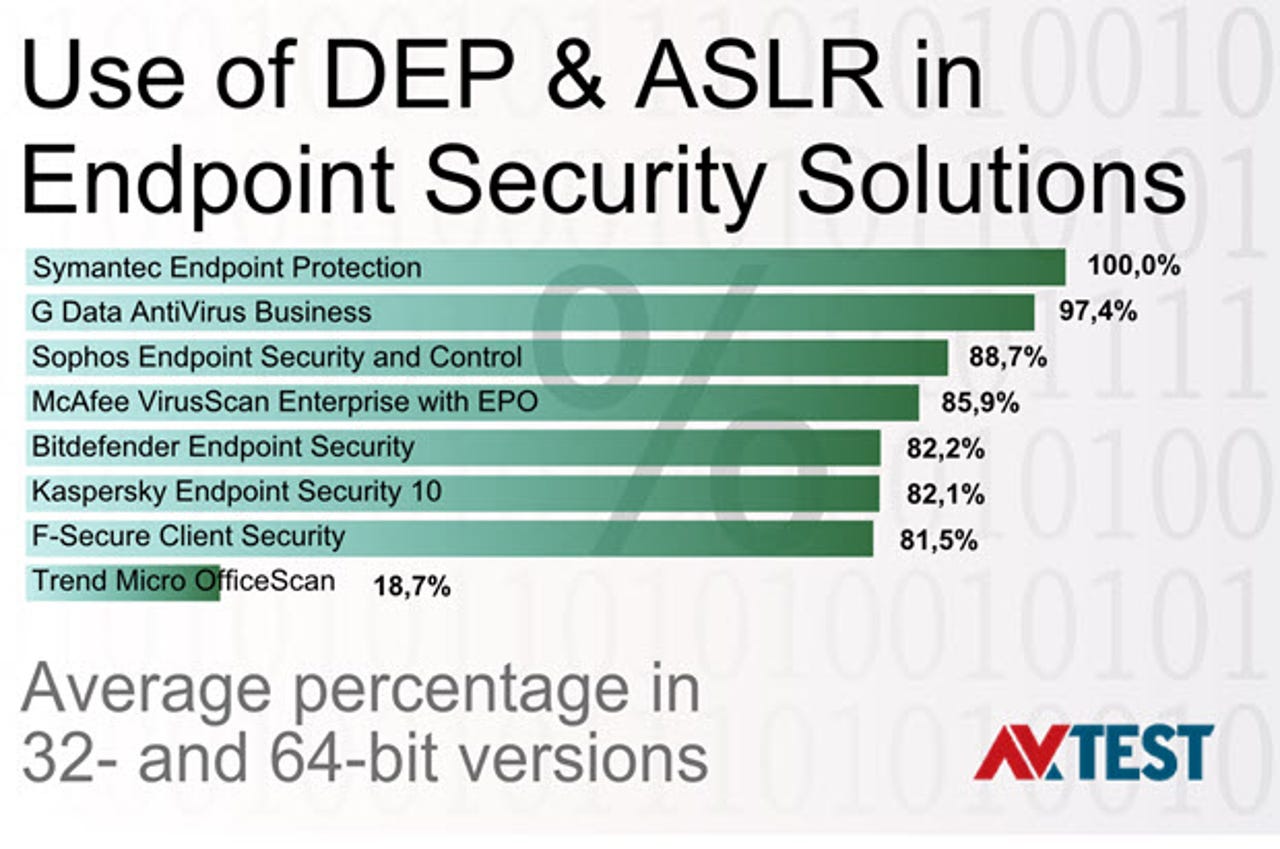
Among the consumer products AV-Test checked, only Eset Smart Security 8 marked 100 percent of executables for both DEP and ASLR, although both Avira Antivirus Pro and Norton Security were over 99 percent and eight more products were above 90 percent. Among the eight business endpoint security solutions examined by AV-Test, only Symantec Endpoint Protection was at 100 percent, with G Data AntiVirus Business close behind. Many products have a shockingly low percentage of protected executables, such as Trend Micro OfficeScan's 18.7 percent and eScan IS's 17.5 percent.
Conceptually, malware and vulnerability exploits are different beasts although, according to Pedro Bustamante, director of Special Projects at Malwarebytes, about 60 percent of new malware is now coming from exploits, mainly of Internet Explorer, Flash and Silverlight, delivered through common exploit kits. The alternative is generally social engineering, i.e. to trick the user into executing a program.
Exploits of anti-malware are not common, but could be a good entry technique for a targeted attack.