Princess ransomware makes a visit to the wrong website a royal mistake

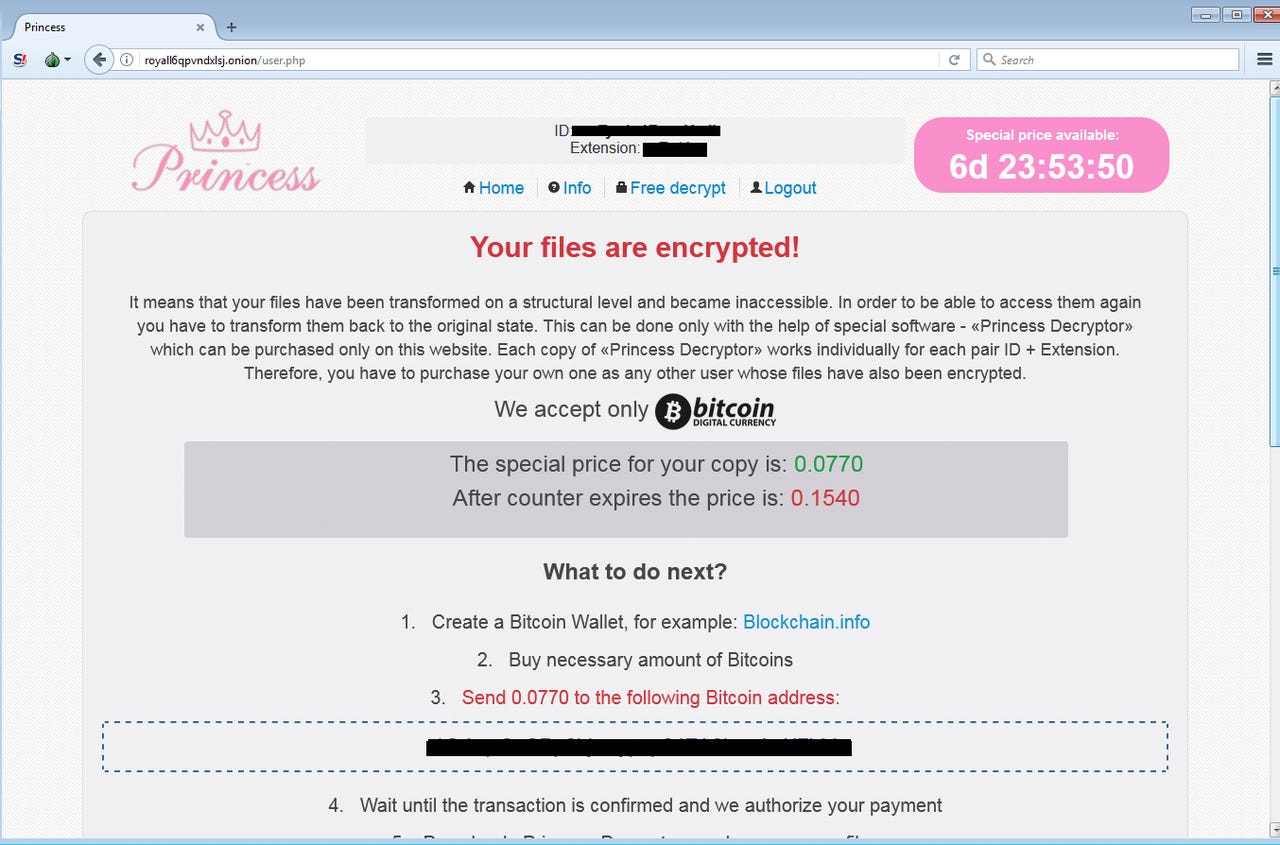
PrincessLocker provides victims with a "special offer" if they pay up within a week.
A newly-uncovered cybercriminal campaign is using a well-known exploit kit to distribute ransomware through drive-by downloads on hacked websites.
Security
While not used as prolifically as it once was, the RIG Exploit kit uses vulnerabilities in Internet Explorer and Flash Player to launch JavaScript, Flash, and VBscript-based attacks to distribute malware to users who have visited a compromised website.
Such attacks were once subtler, used to distribute malvertising to drive click-based revenue or in some instances, spread stealthy malware.
But now researchers at Malwarebytes have uncovered a campaign which is harnessing RIG on hacked websites in order to distribute the Princess/PrincessLocker ransomware.
This particular form of ransomware isn't particularly widespread, but it's notable for initially using the same template as Cerber, one of the most successful ransomware families.
However, researchers have noted that the similarities between the two forms of ransomware are superficial, with the actual code behind PrincessLocker "much different" to that of Cerber.
Upon visiting a compromised website, the user will be directed to a hacked page which is used to take advantage of exploits in order to deploy PrincessLocker onto the system.
The attack vector is different to a ransomware distributor's usual tactic of pushing it in phishing emails, but once the malware is delivered, the result is the same -- the victim's files are encrypted and the cybercriminals demand a ransom in order for them to be freed up.
See also: Ransomware: An executive guide to one of the biggest menaces on the web
PrincessLocker initially asks for a 0.0770 bitcoin ransom ($370/£285) -- a relatively low figure compared to other forms of ransomware -- in return for "special software" to decrypt the files.
The attackers claim that this is a "special price" which is only available for seven days. If a victim waits longer than that to pay the ransom, it rises to 0.1540 bitcoin ($738/£570).
Researchers have previously determined PrincessLocker to be relatively unsophisticated compared to other forms of ransomware. Because of this, a decryption tool is available to crack earlier forms of PrincessLocker. However, the attackers took note of their initial errors and the tool no longer works for the more recent strains.
The best way to avoid negative consequences of PrincessLocker is simply to avoid infection in the first place -- and, with patches for the critical vulnerabilities exploited by the kit having been available for over two years, there's really no excuse for having not applied them.
Related coverage
RIG exploit kit crimewave infects millions
The latest version of the exploit kit is active and has infected 1.3 million people.
Ransomware: Why one version of this file-encrypting nightmare now dominates
Move over Locky; there's a new king of ransomware...
- Ransomware: The smart person's guide [TechRepublic]
- No more ransomware: How one website is stopping the crypto-locking crooks in their tracks
- After WannaCry, ransomware will get worse before it gets better
- Malware now comes with customer service [CNET]
- This malvertising campaign infected PCs with ransomware without users even clicking a link