Ransomware-as-a-service schemes are now targeting Macs too

MacRansom is believed to be the first instance of ransomware-as-a-service targeting Macs.
The first instance of ransomware-as-a-service targeting Mac OS has been discovered for sale on the dark web - allowing low level cybercriminals to target Apple computers even if they have limited tech skills.
While most desktop ransomware targets Windows, simply because it is the most widely used operating system, some ransomware has also been known to target Apple systems.
But while ransomware-as-a-service (RaaS) schemes offering wannabe cybercriminals a doorway into cyber-extortion - in exchange for a cut of the profits for the author - have been common for Windows since last year, they've not been seen to target Macs until now.
Uncovered by cybersecurity researchers at Fortinet, MacRansom is advertised on a TOR web portal and claims to be 'the most sophisticated Mac ransomware ever' and looks to be the first instance of RaaS targeting Mac OS.
MacRansom advertisement on the dark web.
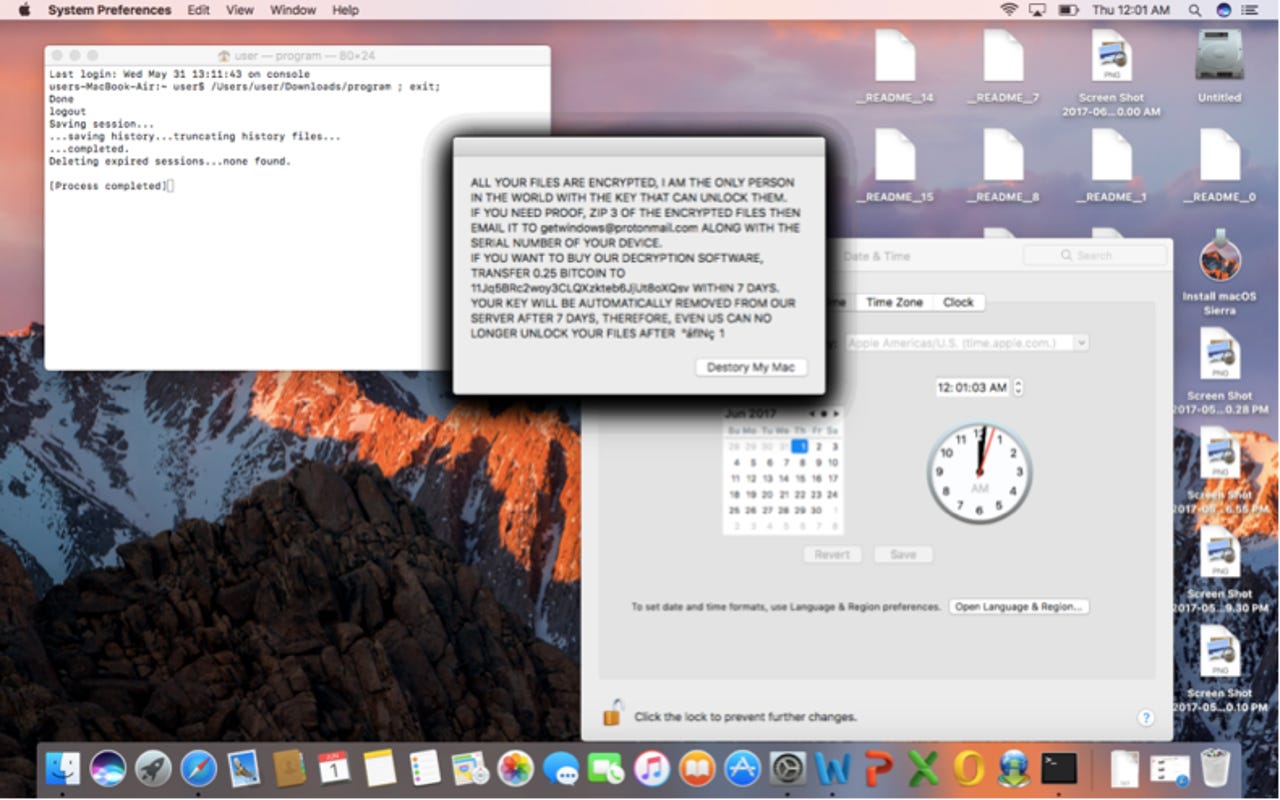
Analysis of the ransomware by researchers shows that it comes equipped with a trigger time set by the author at the request of the scammers that buy the software, allowing the perpetrator to delay the file-encryption, rather than instantly locking the victim out of their files.
Once triggered, MacRansom gets to work, locking down files - although it only encrypts a maximum of 128. Researchers note that this means this piece of crypto-ransomware is not as sophisticated as other OSX crypto-ransomware that have been previously disclosed.
Nonetheless, it's still capable of encrypting files, encrypting both com.apple.finder.plist and the original executable as well as changing the Time Date Stamp. This tactic is used so that even if recovery tools are used, the recovered files are almost useless.
Those infected with MacRansom receive a ransom demand of 0.25 Bitcoins - around $700 - and the threat of all their files being deleted after a week. Those willing to give into the demand need to contact an email address in order to decypt their files suggesting that this isn't an advanced operation.
However, despite what Fortinet researchers describing MacRansom as "far inferior from most current ransomware targeting Windows" it still encrypts files and causes "real damage" to victims.
There's also the worry that the appearance of MacRansom will result in copycat code from others looking to gain a foothold in the relatively uncharted territory that is ransomware-as-a-service targeting Macs.
"MacRansom is yet another example of the prevalence of the ransomware threat, regardless of the OS platform being run," say researchers.
But ransomware isn't the only malicious software the MacRansom authors deal in, researchers at AlienVault have uncovered the same operation dealing in trojan spyware targeting Macs.
The presentation of MacSpy is almost identical to MacRansom.
The free version of the Mac RAT claims to allow users to spy on victims via keylogging, capturing screenshots and acquire any files synced using iCloud.
Researchers note that while MacSpy isn't particularly stealthy, it's still feature rich and shows how malware authors are increasingly targeting Mac OS X.
"People generally assume when they are using Macs they are relatively safe from malware. This has been a generally true statement, but this belief is becoming less and less true by the day," they said.
READ MORE ON CYBERCRIME
- Are Macs safe from viruses? [CNET]
- Ransomware: An executive guide to one of the biggest menaces on the web
- How Bitcoin helped fuel an explosion in ransomware attacks
- Ransomware: WannaCry was basic, next time could be much worse
- Why ransomware attacks are making Bitcoin more expensive for everyone [TechRepublic]