Research: Inconsistent IT policies create BYOD risks, wearable security lags behind smartphones and laptops

A growing number of workers would find it difficult, if not impossible, to do their job without the help of a laptop, smartphone, tablet or, increasingly, a wearable device.
Tech Pro Research (ZDNet and TechRepublic's premium site) conducted an online survey in April and May 2016 to find out what types of security measures IT is taking with mobile devices, which devices professionals think are most secure, and how news about big security breaches affects strategic and purchasing decisions.
BYOD programs widespread, IT support policies mixed
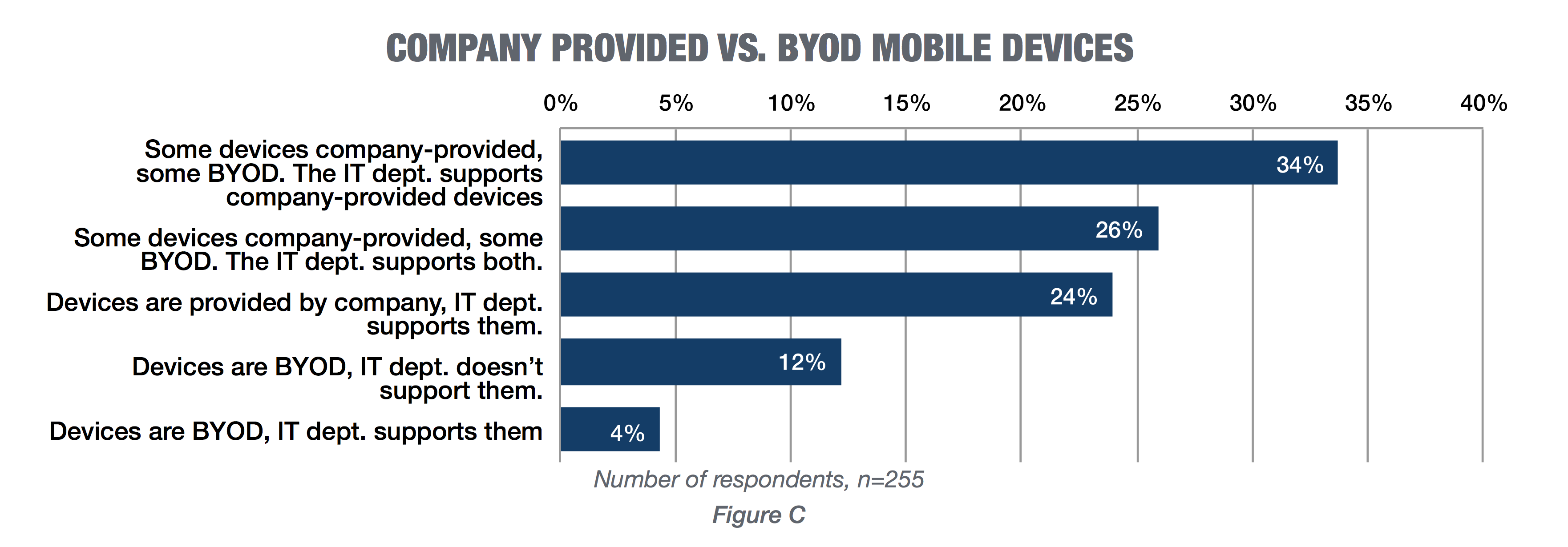
Only 2 percent of respondents said that mobile devices aren't used by employees at their company. Of the 98 percent who reported mobile device use, 94 percent said their companies use smartphones and laptops. Tablets were common as well, at 74 percent. Wearables still have a niche audience, with 14 percent reporting using them. Based on survey results, BYOD is widespread, with 76 percent of respondents saying their company allows employees to use their own devices for work, but IT departments are still divided about supporting these devices. As report author Mary Shacklett said, this represents a significant security risk area.
Wearable security lags behind laptops/smartphones
Security levels varied widely depending on device. Laptops were most likely to have all types of security measures installed. Smartphones were somewhat less likely to have these security measures, but, according to Shacklett:
"The one security practice that was virtually on a par between smartphones and laptops was the management of devices from a central point. Likely, that is because businesses of all sizes recognize the importance of being able to track and lock down lost or misplaced smartphones."
Use of ID and password was still strong on tablets, at 89 percent, but use of the other measures was below half. Wearables brought up the rear in terms of security. Only 57 percent of respondents said their companies require user IDs and passwords, and less than a quarter used data encryption or device management software. A third of respondents whose companies had wearables in use said there were no security measures in place on those devices.
Most believe mobile devices are less secure
The majority of respondents whose companies use mobile devices said they believe those devices are less secure than fixed devices like desktop computers. They gave a variety of reasons. A large part of this group said mobile devices are more at risk because employees can lose or misplace them. Difficulty of securing devices outside company walls was the second most cited reason for believing mobile devices are less secure. Right behind that was the potential for employees to violate security practices and policies.
Very few respondents -- only 12 percent -- had experienced a security breach, but among those who had, the top reason was a device being lost or misplaced. Perhaps this lack of experience with security breaches influenced responses to our question about mobile security data breaches in the news. Over half (57%) of respondents said big cases like the Apple/FBI scuffle don't influence their purchasing or strategic decisions when it comes to mobile security.
Get the full report! Download Tech Pro Research's Mobile Device Research: 2016 security trends, attack rates, and vendor ratings for smartphones, tablets, laptops, and wearables.
Tech Pro Research is the premium content sister site to ZDNet and TechRepublic.