Researcher: 50 percent of Mac OS X users still running outdated Java versions
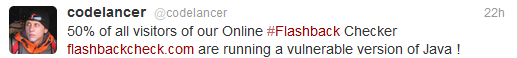
According to a tweet posted by Aleks Gostev, Chief Security Expert, Global Research and Analysis Team at Kaspersky Lab, 50% of the visitors to their newly launched Flashback information site, are still running outdated versions of Java, potentially exposing themselves to numerous exploitation attempts courtesy of malicious attackers.
The cybercriminals behind the Flashback Mac OS X malware are exploiting CVE-2011-3544 and CVE-2012-0507 vulnerabilities in Java, and that's just for starters.
According to Zscaler, hundreds of thousands of enterprise users remain exposed to malicious attacks, due to the fact that they're running outdated versions of their third-party software.
Here's the summary of their findings affecting, both, Mac OS X users and Windows users:
- Adobe Acrobat - 62.54% of out-dated plugins
- Adobe Shockwave - 35.69% of out-dated plugins
- Microsoft Outlook - 7.26% of out-dated plugins
- Java - 5.88% of out-dated plugins
- Adobe Flash - 4.37% of out-dated plugins
- Microsoft SilverLight - 1.73% of out-dated plugins
- QuickTime - 1.71% of out-dated plugins
- Windows Media - 1.25% of out-dated plugins
- RealPlayer - 0.23& of out-dated plugins
A malicious attacker targeting the Mac OS X platform, doesn't need to take advantage of zero day vulnerabilities, due to the fact that end users continue failing to patch their third-party applications and browser plugins. What's particularly interesting in the Flashback Mac OS X malware attack, is the fact that the cybercriminals behind it took advantage of the delayed patch for Java under Apple's OS. Taking into consideration the percentages of end users still using the Web with outdated third-party applications and browser plugins, multiple Flashback related campaigns could be launched relying on this fact.
Apple users, with a patch for the Java vulnerabilities currently available, there's no excuse to avoid patching as soon as possible.