Russian hackers hijack Italian sites to serve exploits

The Russian crime ring behind the infamous WebAttacker/MPack exploit toolkit hacked into thousands of Italian Web sites over the weekend and used a one-line snippet of code to redirect surfers to a server rigged with drive-by exploits.
Around midday today, the server hosting the exploits was live and anti-virus researchers tracking the attacks have found more than 8,000 hijacked Italian Web sites.
The sites at risk cover a wide range of Internet interests -- from cars and racing (likely to take advantage of the formula one weekend), hotels, sports, music, lottery and pornography were all victims. Even web sites connected to Jon Bon Jovi and Mother Teresa weren’t spared, according to virus researchers at Trend Micro.
Here's a diagram of the attack scenario from Trend Micro's Carolyn Guevarra:
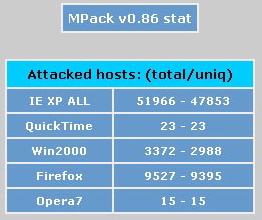
The MPack exploit kit used in this attacks contain a stats counter that spell out in detail the types of exploits used, the number of compromised computers and types of browsers used by the victim (see screenshot above). In this case, it is clear that some newer exploit modules have been added to take aim at flaws in Firefox, Opera and even Apple's QuickTime media player.
Symantec's Elia Floria provides a glimpse at the statistics:
The list of compromised sites is huge and from Mpack statistics this attack is working efficiently (the statistic page reports 65K unique visitors with almost 7K exploited browsers).
It is important to note that the exploits are targeting vulnerabilities that have already been patched so the best defense is to ensure that your machine is fully patched (OS and applications running on top).
Secunia's free software inspector is a nice place to start scanning your machine to look for weak spots. This tool will detect insecure versions of applications installed, verify that all Microsoft patches are applied and assist you in updating your system and applications .