Severe iOS bug prompts iCloud password theft

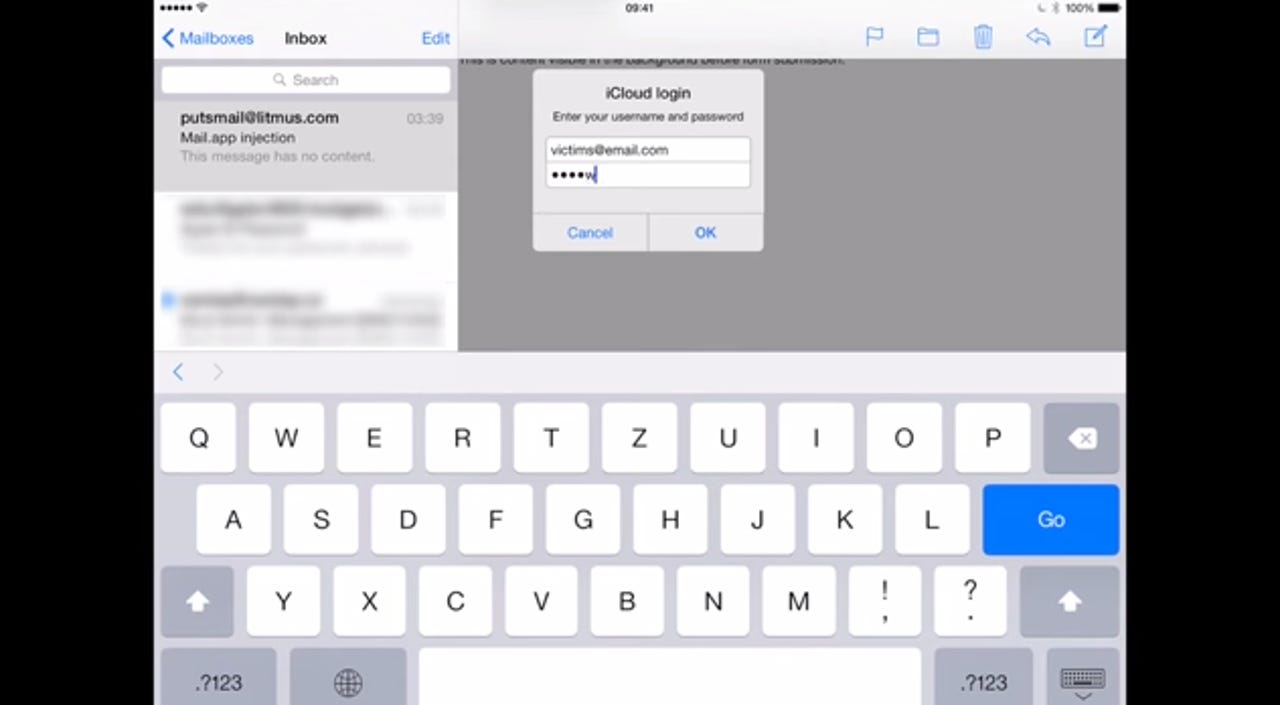
A researcher has published a proof-of-concept of an attack against Apple devices which can result in the theft of iCloud passwords.
The proof-of-concept, hosted on code repository GitHub details the flaw, which is found within the iOS mail client. According to the researcher, the bug does not strip out potentially malicious code such as the < meta http-equiv=refresh > HTML tag in e-mail messages, which allows remote HTML content to be loaded -- replacing the content of the original email for fraudulent purposes.
The proof-of-concept shows an email which, when sent to a victim, brings up a form identical to the iCloud pop-up credentials prompt box. If the email is opened and the victim inputs their credentials, a hacker could steal these details.
The account details are submitted to a customized remote server's .php coding, which in turn saves them to a text file which is eventually sent out to the server controller's email inbox.
All that is required is a server hosting the fake prompt box coding and an email which uses the meta tag to fool an iOS user -- and as Apple's operating system is known to sometimes randomly display login prompts, this type of high-end, sophisticated phishing campaign could be widely successful if left unpatched.
"JavaScript is disabled in this UIWebView, but it is still possible to build a functional password "collector" using simple HTML and CSS," the researcher says.
The proof-of-concept is demonstrated in the video below:
In order to avoid raising suspicion, the exploit includes detection capabilities to ascertain when a victim has already viewed a message, and therefore does not continually display the password prompt. A function called "autofocus" is also used to hide the login dialog once a victim has entered their password in the correct field and clicked the OK button.
The security researcher says he discovered the flaw in January this year and the latest available versions of the iOS operating system on iPads and iPhones are vulnerable. Six months later, a fix has not been issued in any of the updates following iOS version 8.1.2, prompting the decision to release the exploit online.
Updated: "We are not aware of any customers affected by this proof of concept," according to an Apple spokesperson. "But are working on a fix for an upcoming software update."
See also: Apple WWDC 2015: If you want all those cool new iOS 9 features, it's time to buy a new iPad
Essential iPad, iPhone apps for business travel
Read on: In the world of security
- Grabit campaign spies on SMBs, steals sensitive data
- Hola: A free VPN with a side of botnet
- Researchers track commuters using stolen mobile accelerometer data
- Retailers targeted by new point-of-sale malware through job requests
- Ransomware rescue kit released to combat criminal enterprise
Read on: Fixes and Flaws