Sopelka botnet drops Citadel, Feodo, and Tatanga crimeware variants
Security researchers from S21sec have published an analysis of the Sopelka botnet. Operating since May 2012, it is known to have launched five unique campaigns, three of which dropped crimeware variants from multiple families.
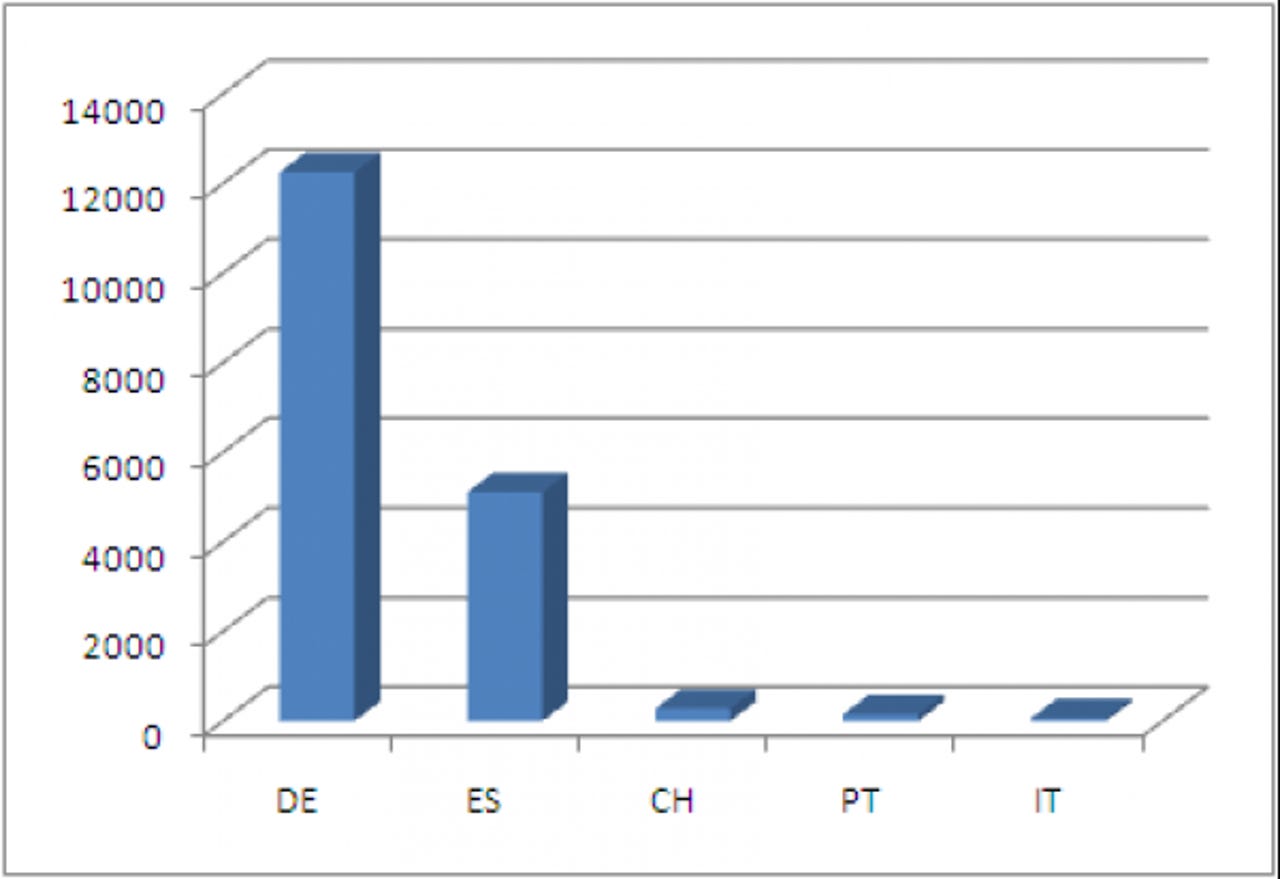
Based on the researchers' data, the group behind the botnet managed to infect over 16,000 hosts, the majority of which were geolocated to Germany and Spain, the two countries topping the infection per countries chart.
Just how easy is it to develop and manage such a botnet for the sake of monetizing the infected hosts, and cashing out in complete anonymity? In 2012, the process of developing and managing such a botnet is entirely automated, efficient, and most importantly - available as a service through a malicious underground Cybercrime-as-a-Service provider.
Sopelka is a typical representative of the "botnets that never make the news" category. Small, resilent, these botnets usually go beneath the radar until their payload starts attracting the attention of vendors and researchers.
What's also worth emphasizing on regarding this type of "aggregate-and-forget" botnets, is the fact that they plan a crucial role in the ongoing cyber warfare arms race, allowing their operators to launch a multitude of cyber operations, and achieve a complete plausible deniability thanks to the way these botnets were used.
What do you think? Will the future of cyber warfare be dominated by small and targeted botnets, or will it be dominated by good old fashioned massive botnets? Would botnets even count in comparison to targeting a single individual through sophisticated social engineering and technical means?
TalkBack!
Find out more about Dancho Danchev at his LinkedIn profile.