Source code for Skype eavesdropping trojan in the wild
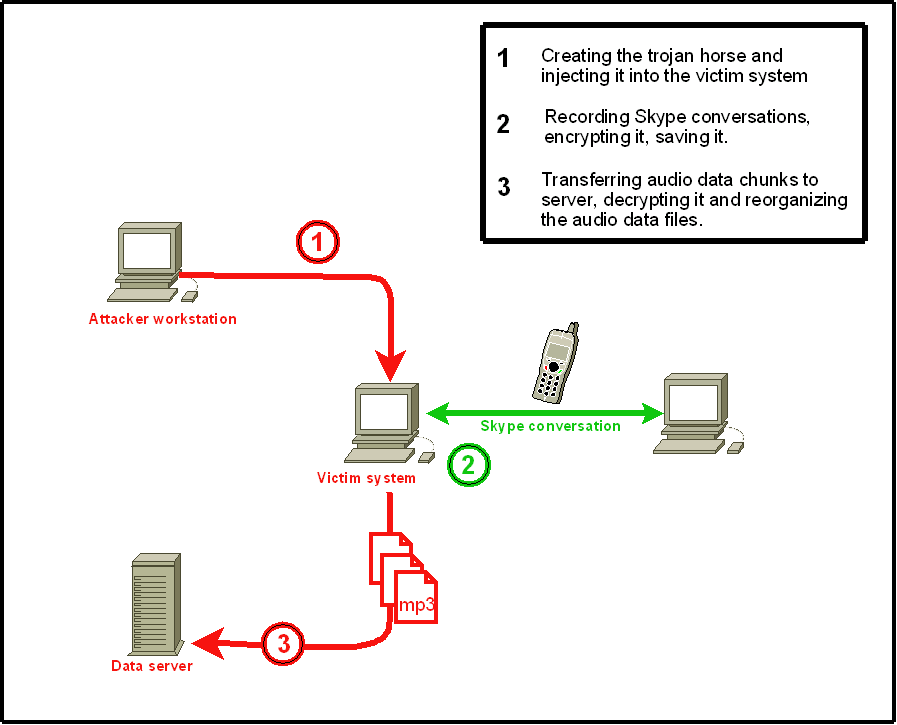
Here's how the trojan, currently detected as Trojan.Peskyspy, works:
"When the Trojan is executed, it injects a thread into the Skype process and hooks a number of API calls, allowing it to intercept all PCM audio data going between the Skype process and underlying audio devices. Note: Since the Trojan listens to the data coming to and from the audio devices, it gathers the audio independently of any application-specific protocols or encryption applied by Skype when it passes voice data at the network level.
Note: The incoming and outgoing audio data are stored in separate .mp3 files. The Trojan also opens a back door on the compromised computer, allowing an attacker to perform the following actions: - Send the .mp3 to a predetermined location - Download an updated version - Delete the Trojan from the compromised computer"
And while some of these governments are reportedly spending surreal amounts of tax payer's money (Rental of the Skype-Capture-Unit per month and instance EUR 3.500) in order to achieve their objectives, others are taking the cost-effectiveness path by attacking the weakest link in the process - the end user infected with a targeted DIY government sponsored spyware recording all ongoing and incoming Skype calls, thereby bypassing the need to attack the encryption algorithm.