Spammers harvesting emails from Twitter - in real time
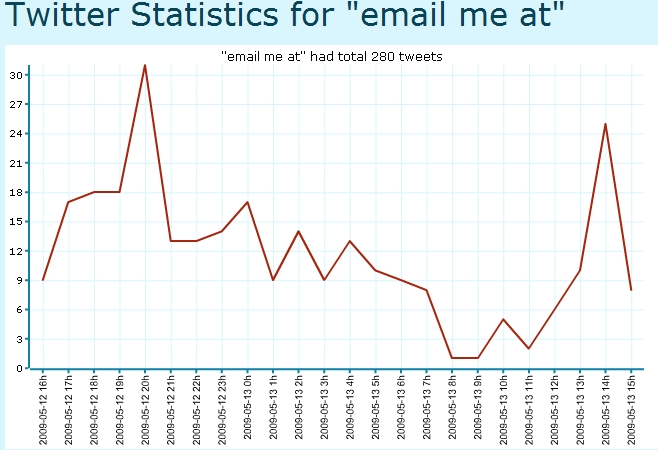
Basically, the search query consists of common phrases such as "email me at" and "contact me at" in a combination with a domain of a spammer's choice.
The result? A flood of valid and fresh email addresses of Twitter users unaware that their emails will not only get indexed by public search engines, but also, that the output can be syndicated for spamming purposes.
Email harvesting has been around since the early days of the Internet, and has therefore greatly evolved throughout the years. From the JS.Yamanner@m worm spreading through a Yahoo Mail flaw in 2006, harvesting @yahoo.com emails from the infected indoxes in order to further propagate, the email harvesting scripts crawling the web and their modern versions, to the Web 2.0 spammer's mentality of harvesting instant messaging and social networking user names - their database usually ends up as value-added service in a managed spam vendor's proposition.
In Twitter's case, their TOS states that:
- You are solely responsible for your conduct and any data, text, information, screen names, graphics, photos, profiles, audio and video clips, links ("Content") that you submit, post, and display on the Twitter.com service
And whereas that should be the case, what Twitter can do to at least slow down this efficient email harvesting approach, is to either allow its users to choose whether or not they would like to have their emails/phone numbers obfuscated (reCAPTCHA Mailhide), or enforce the policy to all users.