Symantec shows Microsoft how to do UAC

Security company Symantec has released a tool that helps to make Vista's UAC (User Account Control) feature clearer and less of a pain to use.
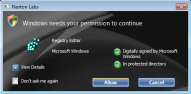
Norton UAC Tool (which, I will warn you right from the start is currently in beta) is a replacement to the UAC prompts that you normally see. It has two usability-related features to offer:
It offers a "Don't ask me again" feature so that the next time you carry out a certain action there's no UAC prompt displayed
It gives you more information about what's triggered a UAC prompt. Specifically:
- Whether the app is digitally signed (and if so, who it is signed by)
- Whether the component resides in a protected directory
Before installing this tool, read the Norton UAC Tool FAQcarefully, especially the following points:
Q: What does Norton Labs get out of my testing? A: DATA! Each time you see a prompt, the Norton Labs UAC Replacement sends meta information about what caused the prompt, and why, to our server. This data will be used, in aggregate, to help Norton Labs build a white list that can be shipped with the UAC replacement and LiveUpdated as needed.
Q: What do you mean by "meta information"? A: The meta information contains file name and file hashes for the EXE that caused the prompt and the EXE that is to be the recipient of the elevated privileges. In addition, the meta information contains file name and file hashes for DLLs that were active in either of the two EXEs, response information (what option did the user choose, how quickly, and did they choose "do not ask me again"), and date/time info.
Also be aware that since this is a beta product, it might introduce vulnerabilities to your system. With that in mind I'd keep this tool off critical systems (or systems connected to critical systems).
Still, it shows that the UAC mechanism can be improved upon, and that a few small tweaks can make the mechanism much more user-friendly.
Thoughts?