Syrian dissidents targeted by malware attacks

The Syrian civil war continues to escalate, and rising levels of violence have not prevented friction from spilling over into the digital world. Rather than clashes limited to the physical environment, pro-government forces are allegedly raising the stakes in a cyberwar against local Syrian dissidents.
According to the watchdog group Electronic Frontier Foundation (EFF), Syrian activists, journalists and members of the opposition are apparently under attack in a new wave of malware attacks aimed at spying on the activities of such groups.
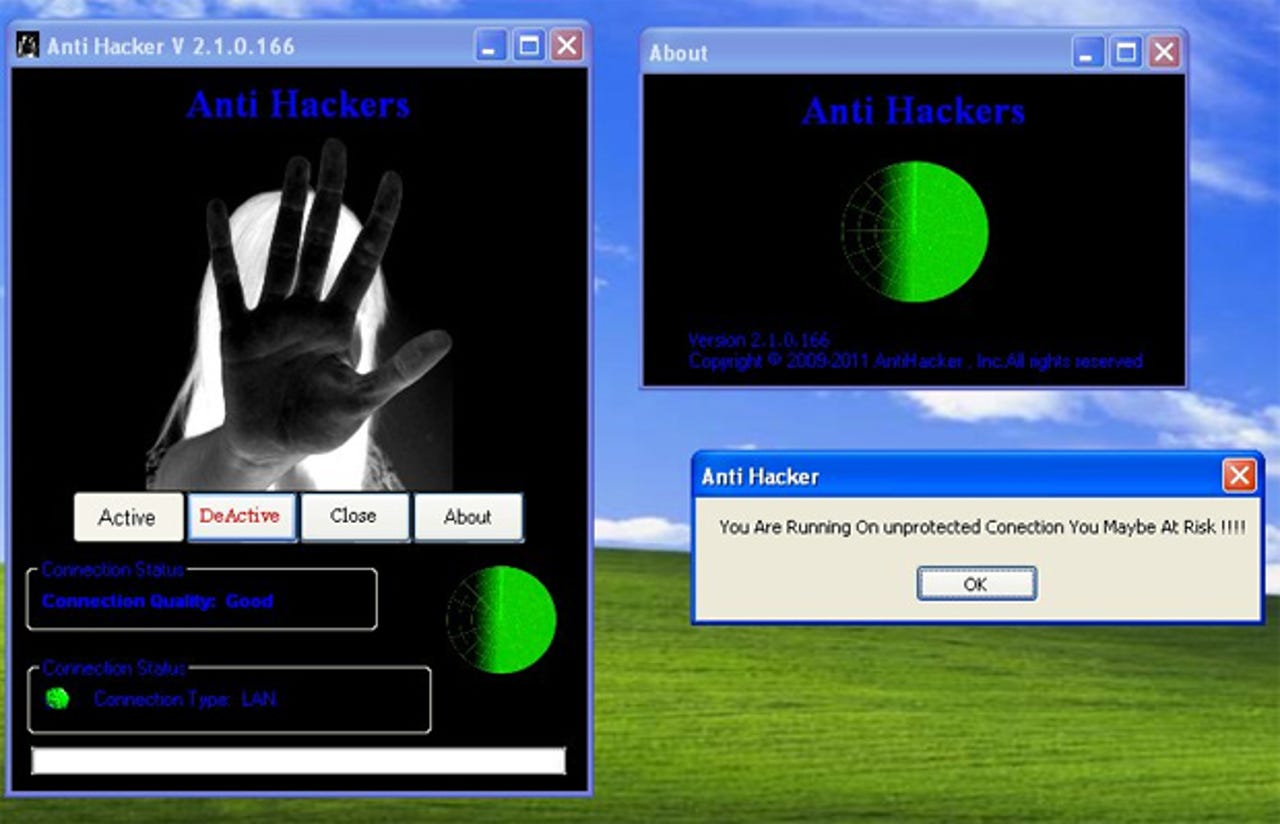
The software, named AntiHacker, subtly installs surveillance software under the guise of protecting personal computers from security breaches and remote attacks. It promises to provide "Auto-Protect & Auto-Detect & Security & Quick scan and analyzing [sic]", but instead, monitors the user covertly.
Through a remote access tool called DarkComet RAT, the attacking party can track the user's moves with a webcam, disable antivirus programs and notifications, delete data and record keystrokes. Instead of fulfilling the promise to protect against hackers and remote attacks, AntiHacker connects back to 216.6.0.28 and attempts to download a program named google.exe. Once downloaded, DarkComet is installed by dropping files into a computer's temporary local files, and a keylogger file is also installed at the same time.
Once the malware has installed successfully, a pop-up appears which states, "You PC is Protect now thank for using our Product [sic]." After analyzing a number of installations, it seems over a dozen versions contain a version of DarkComet.
According to the watchdog, AntiHacker employs a number of methods to lure members of the opposition to install the program, including social media channels like Facebook. However, at the time of writing, the tool's Facebook group was unavailable.
In a statement, EFF's international freedom of expression coordinator Eva Galperin wrote:
"Syrian Internet users should be especially careful about downloading applications from unfamiliar websites. The AntiHacker website showed many signs of being illegitimate, including prolific abuse of English spelling and grammar."
According to EFF, the program cannot easily be detected by antivirus software, but the DarkComet RAT removal tool can be used to detect and remove infections.
Many Syrian activists are becoming aware of the threat digital networks may pose to their cause. On Facebook, the Union of Free Students in Syria group has started an album where students hold up signs warning against phishing attacks and malware.
EFF's analysis of these threats has suggested that this latest development is the work of the same individuals behind previous malware campaigns, including those that that lured targets to use "fake revolutionary documents" and fake Skype encryption tools. These campaigns can be traced back to late 2011.
Image credit: EFF