Talkative botnet herder taunts security researchers

While it is common to find messages and shout-outs buried in virus code, the person(s) behind Nirbot is rather talkative, leaving hostile threates directed at specific individuals, a strange apology for something involving "hospital computers" and even a mock CNN interview that discusses the bot's intent.
The messages are being added to updated versions of the code on a daily basis as the bot author reacts to news stories and blog entries about the attacks, which exploit an old -- and already patched -- buffer overflow in several versions of Symantec Client Security and Symantec AntiVirus Corporate Edition.
Here's a sampling of what's been found in the code so far, via Jose Nazario:
A message aimed at member of the Symantec security research team:
Dear Symantec: For years I have longed for just one thing, to make malware with just the right sting, you detected my creation and got my domains killed, but I will not stop, I can rebuild. P.S. F@?k you assholes, especially Stephen Doherty who is the biggest f@??#t I know of.
This note was found embedded in the code: "Sorry about the hospital computers :(". Researchers believe this is linked to a Nirbot-related attack that infected the Quebec healthcare system.
Another note makes a rather pleasant request that the bot is defined as Irnbot, which the author claims is the true name.
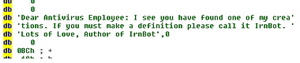
The Internet Storm Center's Johannes Ullrich is also targeted in the code with intimidatory, foul-mouthed threats.
Researchers at the Offensive Computing project noticed a mock CNN interview in the code:
Tonight on CNN: An interview with the author(s) of Rinbot. Who are you? Hacker(s). Are you actually disgruntled? No. Then why are you actively going after Symantec? The worm is designed for getting the highest yield of computers infected, not to aggravate Symantec; there is no hate. So why attack the Symantec anti-virus program? A lot of businesses and universities run the application, making it a prime target for exploitation. Are you aware that your worm is crippling computer networks? Yes that can happen on slow networks or networks with many computers; the worm also searches and removes other worms from the system, acting as a small anti-virus program if you will. If you wish not to have those problems keep your software updated. Why did you taunt Symantec and other security companies? They were the first to list the worm on their site and try and get servers shut down. What do you intent to use the infected computers for? Nothing very malicious; no fraud or anything like that. What is the real name of the worm and how did you come up with it? The real name is IrnBot, it is named after a popular soft drink called IrnBru. Thank you for your time author of Rinbot. You are very welcome CNN, thank you for the opportunity to explain.
Immediately after the text of the CNN interview was posted on the Offensive Computing blog, the IRC (Inter Relay Chat) channel controlling the zombies was changed to #OC and the leet-speak spelling of OffensiveComputing.