The Kneber botnet - FAQ
A recently uncovered network of compromised hosts dubbed, the "Kneber botnet", managed to successfully infect 75,000 hosts within over 2,500 organizations internationally, including Fortune 500 companies as well as Local, State and U.S Federal Government agencies.
How did the botnet managed to stay beneath the radar? Who's behind it? Is it an isolated underground project, or a part of the malicious portfolio of a cybercrime organization diversifying on multiple fronts within the underground marketplace?
Go through the FAQ.
01. Why the name Kneber botnet?
The name Kneber comes from the email used to register the initial domain, used in the campaign - HilaryKneber@yahoo.com. What's particularly interesting about this email, is the fact that it was also profiled in December, 2009's "Celebrity-Themed Scareware Campaign Abusing DocStoc" analysis, linking it to money-mule recruitment campaigns back then.
02. My time is precious. In short, what is the Kneber botnet at the bottom line?
It's a mini Zeus crimeware botnet, one of the most prevalent malicious software that successfully undermining two-factor authentication on the infected hosts (Report: 48% of 22 million scanned computers infected with malware), and is slipping through signatures-based antivirus detection (Modern banker malware undermines two-factor authentication) due to the systematically updated binaries.
03. Who's behind it?
It's a cybercrime syndicate involved in everything from blackhat search engine optimization (blackhat SEO), to client-side exploit serving campaigns, and money mule recruitment campaigns.
04. What were the botnet masters able to steal from the infected hosts?
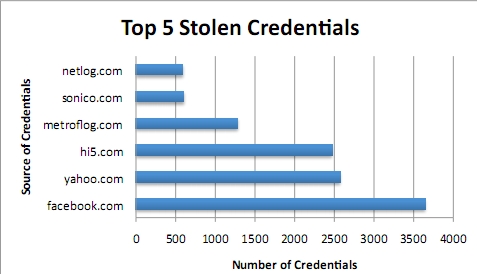
Surprisingly, in the sense that the Zeus crimeware is exclusively used to steal financial data, and hijack E-banking transactions on-the-fly, in the case of the Kneber botnet, researchers from NetWitness found just 1972 digital certificates, and over 68,000 stolen credentials over a period of 4 days.
05. Is this botnet part of a sophisticated cybercrime enterprise vertically integrating by engaging in multiple fraudulent activities, or is it an isolated underground project?
The Kneber botnet is anything but an isolated project, with the individual/group of individuals managing it already connected to numerous malicious campaigns analyzed over the last couple of months. Here are some interesting facts about their activities:
- The name servers used in December, 2009's DocStoc scareware campaign, were registered using the same email used to register the client-side exploit serving domains part of the Koobface gang's experiment conducted in November, 2009. Parked on the same IP hosting the domain which was serving the malware in the campaign, was also the a domain registered to HilaryKneber@yahoo.com (search-results .cn) Even more interesting is the fact that the emails used to registered the rest of the domains parked at this IP, are also known to have been used in registering money mule recruitment domains (Standardizing the Money Mule Recruitment Process; Keeping Money Mule Recruiters on a Short Leash)
- According to the report, the email HilaryKneber@yahoo.com itself was also used to registered a money mule recruitment company known as 24 Hour Express Service
- The report further establishes a connection between the Waledac botnet and this mini Zeus botnet, with the two malware families found simultaneously on the same hosts. An excerpt from the report: "One very interesting observation is that more than half of the ZeuS bots are logging traffic from additional infections on the same host that are indicative of Waledac command and control traffic. Waledac is a peer-to-peer spamming botnet that is often used as a delivery mechanism for additional malware. Additional analysis needs to be conducted, but this raises the possibility of direct enterprise-to-enterprise communication of Waledac bot peers in addition the existing C2 traffic from the Zeus botnet."
- This isn't the first time Waledac connection is established between different botnets - "Waledac is Storm is Waledac? Peer-to-Peer over HTTP.. HTTP2p?"; "Walking Waledac"; "..Conficker downloading the Waledac e-mail worm onto the infected systems"; "..Downad/Conficker box was trying to access a known Waledac domain"
06. What's so special about it?
Moreover, the Kneber botnet is a good example of an ongoing trend aiming to build and maintain beneath the radar botnets (Research: Small DIY botnets prevalent in enterprise networks; Inside the botnets that never make the news - A Gallery; Aggregate-and-forget botnets for DDoS extortion attacks)
And while NetWitness is logically not offering insight into which companies were most affected, but the usual vertical market data, based on 74,000 infected PCs at nearly 2,500 organization, we can assume a proportional scenario with 29.6 infected hosts per company, representing your typical small DIY botnet.
07. What's the OS breakdown of the infected hosts?
The top five affected operating system versions based on the data presented by NetWitness are: XP Professional SP 2, followed by XP Professional SP 3, XP Home Edition SP 3, XP Home Edition SP2 and Vista Home Edition SP 2.
When discussing botnets in general, it's important to keep in mind that botnets aggregated by using the Zeus crimeware, are not the same type of botnets like Conficker, Pushdo or Koobface which rely exclusively on "proprietary malware code". In compassion, due to the fact that Zeus is a DIY (do-it-yourself) type of crimeware, it allows potential cybercriminals to literally generate crimeware variants on their own.