TROYAK-AS: the cybercrime-friendly ISP that just won't go away
Over the past week, security researchers and vendors have been playing a cat-and-mouse game with a cybercrime-friendly ISP known as TROYAK-AS, one of the key "phone back" locations for the command and control servers for the Zeus crimeware serving campaigns for Q1, 2010.
The results so far? A series of attempts by the cybercriminals to restore access to their botnet, and an invaluable learning experience for the community, with the gang exposing node after node of malicious activity.
Why is TROYAK-AS's take down so important at the bottom line?
Disrupting the ISPs activities doesn't mean that the remaining and currently active Zeus campaigns would be somehow disrupted. This common misunderstanding stems from the Zeus crimeware wrongly perceived as a botnet similar to, for instance, the Conficker botnet. In comparison, Zeus is a DIY crimeware -- also available as a managed crimeware service since 2008, perhaps even earlier -- with an unknown of cybercriminals operating their own Zeus botnets.
Taking it down means undermining the effectiveness of a huge percentage of their campaigns launched during the first quarter of the year. Not only does this mean disruption of their operations, but most importantly, loss of confidence on behalf of their customers in TROYAK-AS's ability to stay online.
- Go through analysis of Zeus crimeware serving campaigns using TROYAK-AS's services for Q1, 2010: Outlook Web Access Themed Spam Campaign Serves Zeus Crimeware; Pushdo Serving Crimeware, Client-Side Exploits and Russian Bride Scams; PhotoArchive Crimeware/Client-Side Exploits Serving Campaign in the Wild; Tax Report Themed Zeus/Client-Side Exploits Serving Campaign in the Wild; Keeping Money Mule Recruiters on a Short Leash - Part Two
Ironically, a representative from TROYAK-AS's, your typical cybercrime-friendly virtual neighborhood, is doing his best to retain their underground reputation, by attributing the shut down to the fact that they forgot to pay their upstream provider. Moreover, Roman Starchenko's comments -- fake name that's for sure -- demonstrate the harsh reality in respect to fighting cybercrime internationally, in particular the lack of cooperative efforts into going after the people, not the networks:
- "I know, some of [the] clients of our service might be used for something you called 'botnet'. Anyway, we did not receive any letter from any officials of our country, so will not perform any actions as our law said."
As of Wednesday, March 10th, 2010, TROYAK-AS made multiple attempts to find an upstream provider, temporarily relying on the following ones:
- AS44051 - YA-AS Professional Communication Systems
- AS8342 - RTCOMM-AS RTComm.RU Autonomous System
- AS25189 - NLINE-AS JSC Nline
- AS12993 - DEAC-AS
Today, TROYAK-AS is "de-peered" again. However, contingency planning is clearly part of the provider's quality assurance process, especially in times when the days of the "sitting duck" cybercrime-friendly ISPs are nearly over.
What are TROYAK-AS's customers up to?
Clearly, some of them have lost confidence in TROYAK-AS's ability to remain online, and on Friday, March 12th, 2010, resumes their malicious operations by launching another campaign - "Scareware, Sinowal, Client-Side Exploits Serving Spam Campaign in the Wild". In reality, their customers have a pretty diverse choice of providers offering services similar to those of TROYAK-AS, with cybercriminals offering a mix of legitimate and purely malicious infrastructure for anything cybercrime related.
- Go through related posts on previously shut down cybercrime-friendly ISPs: With or without McColo, spam volume increasing again; Atrivo/Intercage's disconnection briefly disrupts spam levels; Google: Spam volume for Q1 back to pre-McColo levels; Overall spam volume unaffected by 3FN/Pricewert's ISP shutdown
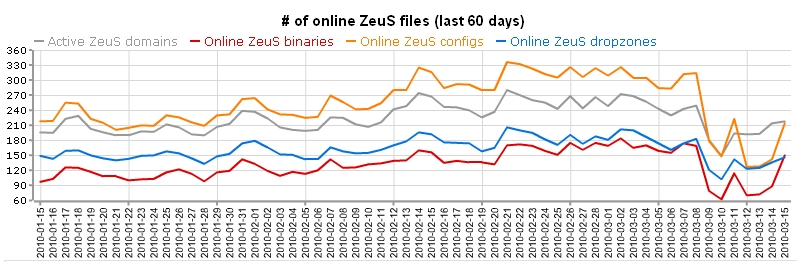
TROYAK-AS remains "de-peered". It's only a matter of time before they find another upstream provider. The ISP remains the tip of the iceberg, with Russia, followed by China and the U.S listed as the top Zeus malware hosting countries.
UPDATE, Wesnesday, March 17, 2010: Today, the folks at RSA FraudAction Research Lab posted an update "AS-Troyak Exposes a Large Cybercrime Infrastructure", offering an insight into the infrastructure that the cybercriminals exposed on their way to put AS-TROYAK back online.
What do you think? Are such take downs relevant in the long-term, or is the "learning experience" gained worth the efforts? Does it really matter if a particular botnet gets shut down, given the fact that the botnet masters remain at large, and would basically aggregate a new one?
TalkBack.