Twitter data theft: the human element

Data security hit center stage this week following the theft of confidential personal and business information belonging to Twitter and it founders. A hacker gained access by infiltrating a Twitter founder's email account protected by weak password security.
This breach raises issues about Twitter's maturity as an organization, particularly concerning security practices, but also paints a black eye on cloud computing in general. Enterprise blogger, Jeff Nolan, commented:
If Twitter were using something other than a public cloud for their documents and messaging, well it would have been a hell of a lot more difficult for someone to login with a password retrieved via the recovery feature in Gmail.
However, ZDNet's Editor in Chief, Larry Dignan, dismisses any notion this situation represents a general cloud computing problem:
Bottom line: Twitter used an easy-to-guess password and recovery question. That’s how the hacker was able to get in - not because Google has some sort of security hole.
THE PROJECT FAILURES ANALYSIS
To place the matter in context, consider the broader subject of data breaches. The following diagram from the I've Been Mugged blog, which covers data breaches and identity theft, illustrates the basic truism that most folks consider security a hassle:
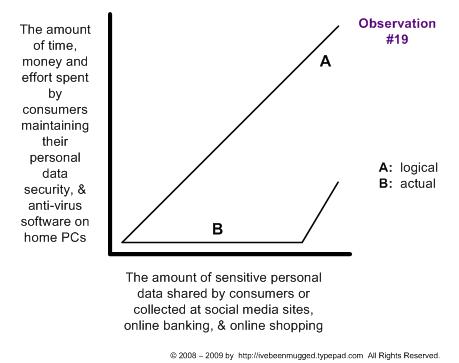
Inconsistent attention to basic security practices is hardly limited to individuals and small companies like Twitter. Some of the largest, most well known organizations in the world have suffered serious data breaches for reasons that seem mind-bogglingly dumb.
A few examples:
- A Bank of Ireland employee lost an unencrypted USB memory stick containing personal information belonging to 894 customers.
- A stolen laptop belonging to consulting firm Deloitte contained confidential personal data belonging to 150,000 UK railway workers and all UK Vodafone staff with pensions.
- Poor system testing caused a medical records privacy breach affecting over 200,000 members of Georgia Blue Cross and Blue Shield.
- A laptop containing confidential information belonging to employees and suppliers of UK newspaper, the Daily Mail, was stolen.
- The Bank of New York (BNY) Mellon lost two sets of unencrypted backup tapes containing private data belonging to 4.5 million individuals.
- HSBC, the UK’s largest bank, lost an unencrypted data disc containing the names and insurance information of 370,000 customers.
Combined with the Twitter incident, these examples illustrate the ubiquity of security breaches. All these cases share a common human failing: poor judgment, carelessness, or insufficient care paid to security.
My take. Although I do believe cloud computing offers greater security risks than on-premise systems, this security failure was not born in the cloud. No, it was created by an open corporate culture that just didn't pay sufficient attention to security.
Update 7/16/09 12:00: Jeff Nolan, quoted earlier, responded to this post in an Enterprise Irregulars discussion. Although he agrees the human element remains king, Jeff also expects more from technology:
You are 100% correct, human behavior trumps technology. However, mature systems, which Gmail surely is at this point, are supposed to take into account human behavior in their user experience. The human failing exists on both sides of the fence: the Twitter administrative employee failed by picking a weak password that was easily guessed and Google is equally culpable for allowing a weak password to be picked for a system used by businesses.
The lesson learned at Google in this experience should be that their identity/authentication system needs to fork. The enterprise edition of Google Apps needs another layer of control that forces users to pick stronger passwords, change them often, and have an alternate retrieval function.
Jeff nails the bottom line: well-designed software should help protect users from poor practices, to the extent possible. In areas such as password control, traditional enterprise software has been doing this for years.